How to Check Disk Space Linux Using du and df
Disk space Linux problems creep in silence. Growing log...
A DDoS stands for Distributed Denial of Service attack is a malicious cyberattack used to disrupt normal network traffic to a server, system, or service to the target with a flood of Internet traffic. Meanwhile, early detection and response are important in minimizing the damage caused by a DDoS attack.
In this post, we will guide you through various methods to check DDoS on Linux servers and understand the cause of attacks on your system.
When it comes you understanding detection methods it is important to know the different types of DDoS attacks:
For a more detailed guide on DDoS refer to What is DDoS? How to Protect your network from it?
Recognizing the signs of a DDoS attack is important for early response. The common indicators of DDoS systems include the following:
Linux offers several built-in tools and commands to help you monitor server health and detect potential DDoS attacks:
1. Monitoring Server Load
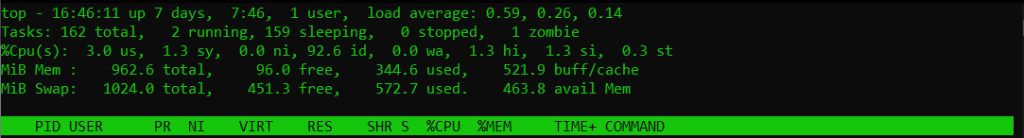
The following command provides a real-time view of system processes and resource utilization.
top
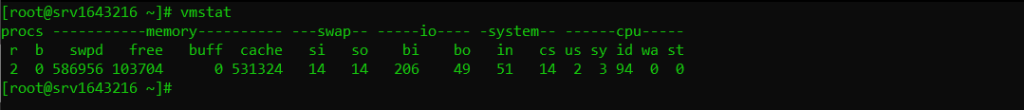
Another Linux command that displays virtual memory statistics including CPU activity and disk I/O.
vmstat
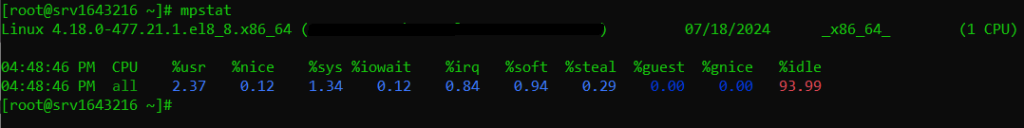
If you want to check CPU statistics including idle time and user/system time. Type the following to check DDoS attack:
mpstat
2. Checking Network Load
If you want to check the load of your network use the following command to display network interface configuration and statistics.
ifconfig
Secure Your Work with Our DDoS Protected VPS!
The best DDoS protected VPS hosting is available with us with no extra fee, Protect your business or online service from 3500+ Gbps DDoS attacks.
Another command provides information about network connections, routing tables, interface statistics, connections, and IP packet statistics.
netstat -stat

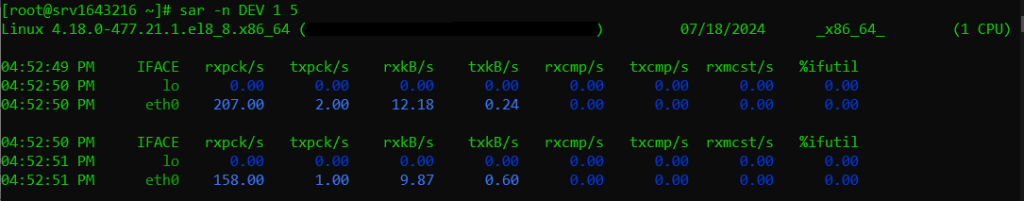
You can also use this command to check reports on system activity for a specified interval.
sar -n DEV 1 5
3. Analyzing Network Traffic
In Linux systems, there are also other options to capture the network packet for analysis.
tcpdump -i eth0 -s 0 -w capture.pcap
If you are comfortable with a graphical interface you can use Wireshark which is a graphical network protocol analyzer that can be used to inspect captured packets. To install this software refer to our guide on how to install Wireshark on Ubuntu system.
You can also configure iptables firewall rules that can be used to filter traffic and block potential attackers.
4. Identifying Suspicious IP Addresses
The following tools that can be used to DDoS check or identify suspicious IP addresses:
5. List Connecting IP’s
Analyzing connecting IPs can still provide valuable insights into potential attack vectors but it is important to understand that DDoS attacks often involve a massive number of IPs, making it challenging to manually analyze the list or attackers can use dynamic IP addresses or proxies to mask their origin.
The netstat command is a versatile tool for viewing network connections. To list the IPs connected to your server:
netstat -ntuap | grep :80
Replace the port number with the port your service is listening on for example 80 for HTTP. This command will list TCP connections numerically along with the process using the port.

Your web server’s access logs can provide a detailed record of incoming connections. Common web server logs include:
/var/log/apache2/access.log/var/log/nginx/access.logYou can use tools like grep, awk, or sed to extract IP addresses from these logs. For example:
grep -h "your_ip_address" /var/log/apache2/access.log /var/log/nginx/access.log | cut -d ' ' -f 1
This command searches for your server’s IP address in both Apache and Nginx logs and extracts the connecting IP.
If you have iptables configured to log connections you can analyze the log file:
iptables -L -nv --line-numbers
To view the log:
less /var/log/iptables/iptables.log
Once you have a list of connecting IPs you can use tools like uniq and sort to identify frequent attackers:
cat access.log | cut -d ' ' -f 1 | sort | uniq -c | sort -nr
This command counts the occurrences of each IP address in the access log and sorts them by count in descending order.
For more in-depth analysis and protection consider these advanced methods:
The following are some important considerations for DDoS detection and mitigation:
Detecting and mitigating DDoS attacks requires a combination of tools, knowledge, and proactive measures. By closely monitoring your Linux server understanding the signs of an attack and implementing appropriate countermeasures you can significantly reduce the impact of DDoS incidents on your system and services.
Elevate your business with Ultahost NVMe hosting that provides significantly faster data access speeds compared to traditional storage options. This means your website will load faster resulting in a smoother user experience and potentially higher conversion rates.
A DDoS attack floods your server with traffic to make it slow or unavailable.
Look for unusual traffic spikes, slow performance, or server unavailability.
Use tools like Netstat, Wireshark, and IPTraf to monitor network activity.
Mitigating a DDoS attack often involves using firewalls, traffic filtering, and DDoS protection services.
Regular monitoring helps detect and respond to DDoS attacks quickly minimizing damage.