How to Fix ERR_SSL_VERSION_OR_CIPHER_MISMATCH
The internet is set on secure connections. When you enc...

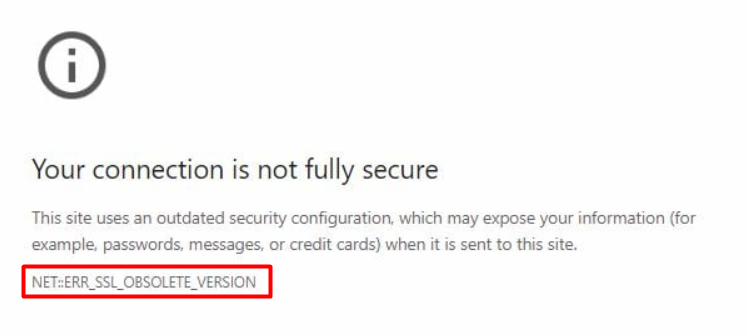
When a website is using an outdated and insecure version of the SSL/TLS protocol, Google Chrome will display the red ERR_SSL_OBSOLETE_VERSION warning. Then, Chrome will block you from viewing the website since this adds to your risks as the user. The warning is there to prevent you from viewing the site until the server makes upgrades to its security configuration.
This concern is in everyone’s best interest, both for website owners and website visitors. In the case of website visitors, it informs them the connection is insecure and can expose their data. For website owners, it causes a loss of user credibility, loss of traffic, and ultimately can affect their search placement. Additionally, when a website shows “not secure”, a user is more than likely to bounce off the site without any engagement at all and they will not return, or if they do, it is not likely.
The ability to know about this warning, and perform your due diligence, can go a long way to ensuring all users have a safe and trusted web experience.
A warning in Chrome indicates that the website is using an old version of the Transport Layer Security (TLS) protocol – TLS 1.0 or TLS 1.1, both of which are insufficient in terms of encryption and security by today’s standards. These versions lack the minimum standard for encryption on browsers today.
This warning usually occurs when you try to visit a site that has not updated the SSL or TLS configuration on its server. Administrators may also see this warning when managing websites on a server which is using an old SSL or TLS protocol. Chrome will display this warning to make users aware they may be creating an unsafe connection unknowingly.
In version 84 and higher of Chrome, more strict standards have been enacted, which forces users to use a website that has updated TLS. This warning makes it difficult for users to bypass, and serves to indicate that Google wishes to have strong encryption standards and safety for their use.
Securing your Website with an SSL Certificate!
Ultahost SSL allows you to encrypt all the data between a visitor and the server with high-quality encryption makes sure that every packet is unbreachable.
Google Chrome has blocked outdated versions of SSL/TLS to reduce known security risks to users and help to promote changes in safer browsing standards. Older SSL and TLS protocols have known issues that can expose data to various attacks and do not support the encryption methods for secure communications.
TLS 1.0 and TLS 1.1 are noticeably lacking support for strong encryption algorithms. Both of these protocols were designed over 20 years ago and can’t protect against modern threats, with quite a few known exploits for these versions:
Websites still using these versions may be exposing user data that is being sent over a network. It would be too easy to intercept login credentials, personally identifiable information, or payment information. The end result of all this is that secure connections will fail, and users will be left at risk.
In order to assist with a shift for browsers to improve security standards, Google blocked support for TLS 1.0 and 1.1 starting with Chrome 84. This coincides with the trend that the wider industry has seen to enforce HTTPS and change to stronger encryption algorithms. Firefox and Microsoft have also made similar changes in supporting newer SSL/TLS protocols.
By explicitly flagging decommissioned SSL protocols, Chrome now allows browsing sessions to be conducted fairly safely with only the risk of connecting to a website that is following today’s standards in security practices. Users now have a significantly reduced chance of data regarding leaks, phishing, or unauthorized access of any sort in browsing sessions.
Checking which SSL version is in use can help troubleshoot and remediate the err_ssl_version_or_cipher_mismatch chrome warning. Several methods are available to help check a website’s TLS protocol status using both browser-based and external tools. These checking methods help developers, site owners and regular users to check that a secured connection meets current security standards.
Google Chrome offers rapid access to the SSL information with its Developer Tools. Click to the page, open the Inspect panel, and go to the Security tab. The Security tab presents primarily the important details about the connection, as well as the TLS version being used. If the connection is based on TLS 1.0 or TLS 1.1, Chrome will warn the user regarding this. This method is used when checking your website or browsing the web while on a site.

External tools can provide a more comprehensive analysis of a site’s SSL configuration and security posture. Qualys SSL Labs is a reputable tool that will scan a domain and provide a full report, including the TLS versions supported, certificate status, and server configuration.
Another useful tool is Why No Padlock, which will test for outdated SSL settings and also check for mixed content issues. Both of these tools are free, and do not need technical knowledge to use. They are commonly used for identifying security weaknesses on public facing websites.
For individuals with server access, it may also be possible to interact with the server using a command line tool like OpenSSL. By doing command-line connection testing with OpenSSL against a domain, individuals can see which TLS version is negotiated. The output will tell the users whether the server is using a secure, current protocol such as TLS 1.2 or TLS 1.3, or if it is falling back to old components that are deprecated.
This is useful for determining whether the server is capable of fulfilling requirements for modern security. It is still important to apply open eyes in diagnosing potential configuration issues that could be on the server-side.
The steps required to remedy the ERR_SSL_version_or_cipher_mismatch warning will also depend on whether you are the owner of the website or simply trying to visit it. As an owner, you will have to fix the server configuration, while users can focus on basic troubleshooting steps.
The warning you are seeing occurs with websites that are using a deprecated TLS version. In order to stop the warning, you will have to ensure your server does not support, instinctively enabling your clients to use an updated, secure protocol.
To start, you will want to look at the TLS configuration on your server. For example, you will want to determine if TLS 1.2 or TLS 1.3 protocol is enabled and disable legacy protocols; TLS 1.0 and TLS 1.1. This can help you confirm that your server is using TLS 1.2 or TLS 1.3 by viewing server logs, use the developer tools in your Web browser, or use an SSL test service.
The next step will be checking and updating your server configuration files. If you are using the Apache HTTP server, you will want to adjust your server ssl_conf or your httpd.conf file to only allow your server to ignore insecure protocols. If you are running NGINX, similarly to Apache, edit the nginx.conf file of your server to include only TLS 1.2 and/or TLS 1.3 in the ssl_protocols directive. If you are working on IIS, disable legacy protocols either via the Windows registry or utilizing a management tool to make your consultation.
Here is a guide to understand about How to Generate a CSR for Apache/Nginx with OpenSSL.
Make sure that both your OpenSSL library and your server package are up to date. An outdated version of OpenSSL may cause your server settings to default to insecure protocols. Most modern operating systems have related package managers (apt, yum or Windows Update) to assist you with installing the latest version. Then, either eliminate the legacy protocols from the operating systems themselves.
If your SSL certificate was issued before you upgraded your TLS settings, it may be worth considering whether to renew or reissue it. While most certificates will still work, some may require regeneration to fit with your updated security settings. Having both certificates and server software up to date ensures compatibility with browser security requirements.
If you are observing this error while attempting to visit a site, there is a high degree of likely that the issue lies with the site’s server, but there are things you can do.
Try to open the website using incognito mode or clearing your browser cache. It can sometimes happen that cached data conflicts with your updated security settings, and leads to false warnings.
If the error still persists, there is nothing else you can do to bypass the warning safely. In this situation, you can contact the site administrator and inform them about the warning. The warning may disappear after they upgrade their server’s TLS settings.
By taking these steps, you will be protected while on secure websites and assist website owners with SSL errors that negatively impact user trust and site performance.
A properly configured SSL/TLS configuration increases website security, helps with browser compatibility, and limits errors like ERR_SSL_ersion_or_cipher_mismatch chrome. There are several recommendations which will establish compliance while keeping a secure environment.
Support for obsolete protocols should be entirely disabled. TLS 1.2 and TLS 1.3 provide strong encryption, while being compliant with a known good security standard. TLS 1.2/1.3 work in all modern browsers and limit the possibility of downgrade attacks. There is no longer any reason to use TLS 1.0 or TLS 1.1.
Learn also Setting Up SSL / TLS on your Cpanel VPS Hosting.
Manual renewing of certificates can lead to surprise expirations, resulting in access issues, leading to a loss of trust. Use vendors like Certbot or Hosting platforms with built-in automated features to automate certificate renewing. Automation provides unbroken HTTPS protection as well as keeps you SSL certified at all times.
Let’s Encrypt provides free trusted certificates, automated issuing and renewing. For users who do not want to bother as much, managed SSL services by web hosts, or CDNs do all of this for you, from beginning to end as well as ongoing management. Both will reduce your risk of incorrect configuration issues, or forgetting to renew certificates.
Utilize online tools like SSL Labs’ SSL Test to analyze the encryption configuration of your site. These tests will also show you the TLS versions supported, the strength of your ciphers, and possible configuration vulnerabilities. You should regularly test in order to find the problems earlier; plus, validators will assure you that your configuration is current with today’s browser and industry standards.
The presence of the chrome err_ssl_version_or_cipher_mismatch warning is a good reminder that you must make sure you are using modern and available SSL / TLS protocols. This warning indicates that a website is using legacy encryption methods such as TLS 1.0 or TLS 1.1, which are significant security issues. Google Chrome blocks these sites to prevent attacks such as POODLE and BEAST. Because we request updates to the server configuration that only supports TLS 1.2 or 1.3, upload the required encryption protocols and make sure the validity of SSL certificates.
It is vitally important for both users and website owners to resolve this error. Users should check their browser for updates when they receive warning messages, and users should resist bypassing security warnings. Website administrators must keep up with contextually relevant guidelines for SSL or TLS best practises, ensure they are renewing certificates automatically, and ensure they are performing price security tests at regular intervals. All of these steps will help maintain trust, improve site performance, to help keep with browser security policies.
Is your website encountering the “ERR_SSL_OBSOLETE_VERSION Chrome Warning” error? Upgrading to an Ultahost secure web hosting plan empowers you with an environment that offers control panels allowing you to install an SSL certificate on your website.
This warning appears when a website uses outdated TLS protocols like TLS 1.0 or TLS 1.1 that Chrome no longer supports.
No, Chrome does not allow bypassing this warning to protect users from insecure connections.
Chrome supports TLS 1.2 and TLS 1.3, which offer stronger encryption and meet current security standards.
They need to update server settings to support only TLS 1.2 or 1.3 and disable older protocols.
Not necessarily. It usually indicates outdated server configuration, not a security breach.
In most cases, no. But if the certificate is outdated or incompatible with new TLS settings, renewal may help.
Yes, browsers like Firefox, Safari, and Edge have also dropped support for TLS 1.0 and 1.1.