How to Install Maven on Windows
Apache Maven is a project build automation and dependen...
Configuring the Windows Server 2012 Firewall is an important aspect of maintaining network security and ensuring the proper operation of your server. Firewalls help control the flow of traffic to and from your server, allowing you to protect it from unauthorized access while still enabling necessary communication.
In this post, we will discuss the steps to configure Windows 2012 Firewall Server which allows you to keep the server secure and ensure that it operates smoothly.
Firewall configuration is an essential task for any system administrator. Windows Server 2012 includes the Windows Firewall with Advanced Security, which provides enhanced security features for managing inbound and outbound traffic. Before setting up firewall configuration, let’s understand the fundamental concepts:
Following are the steps to setting up Windows 2012 Server Firewall for security purposes:
First, you need to open the Firewall Management Console of the Windows 2012 server. Press the Windows key + R to open the Run dialog box. Type wf.msc and press Enter.
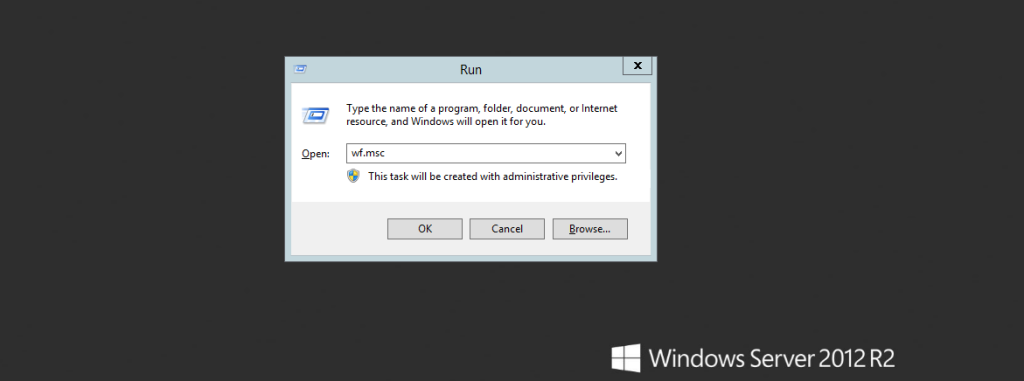
This opens the Windows Firewall with the Advanced Security console. The console provides an overview of the firewall status. It includes sections for Inbound Rules, Outbound Rules, and Connection Security Rules.
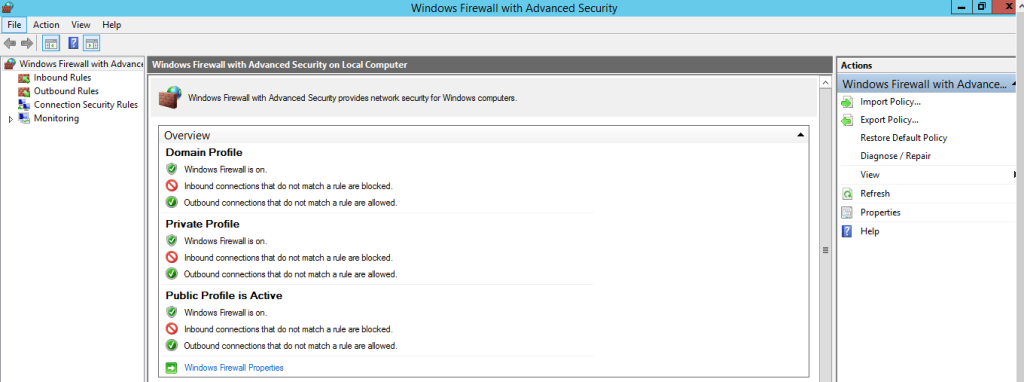
Inbound rules control the traffic that is allowed to enter the server. Here’s how to configure them:
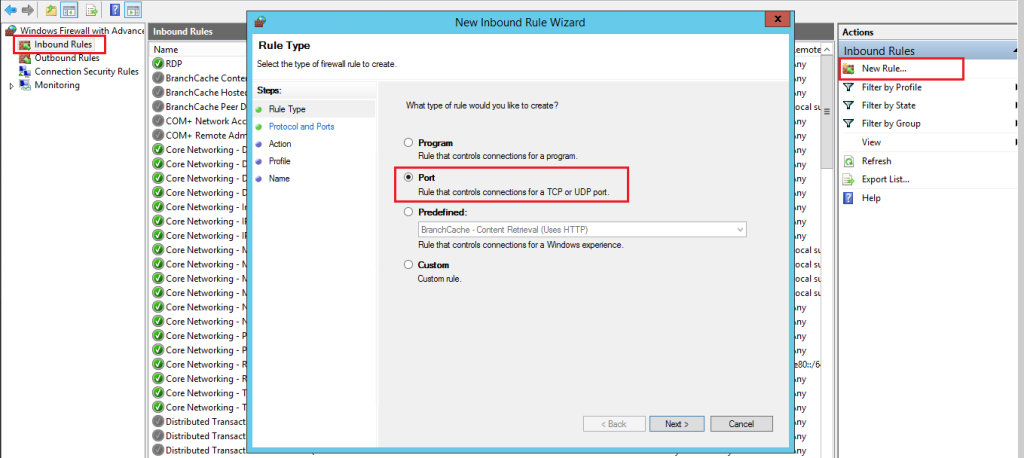
To create a new inbound rule, Click “Inbound Rules” in the left pane. Click on “New Rule…” In the right pane. This opens the New Inbound Rule Wizard.
Select the type of rule you want to create. Common types include:
To configure port rules, select “Port” and click “Next”.
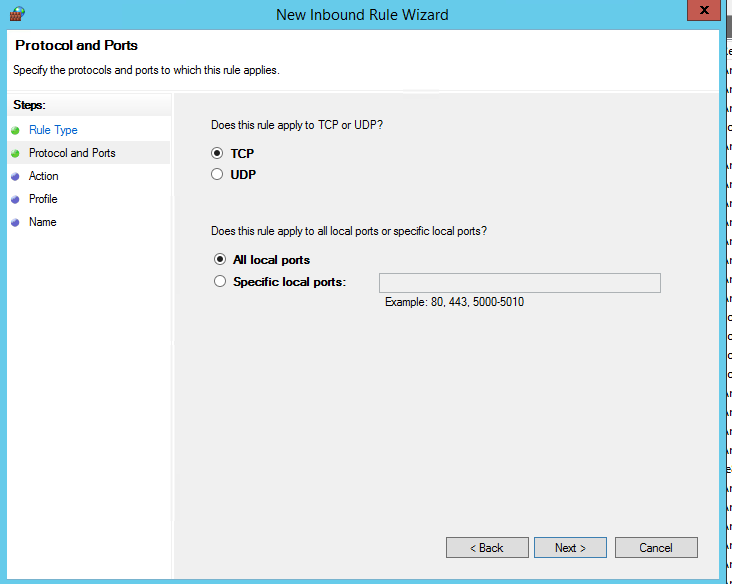
Choose whether the rule applies to “TCP” or “UDP”. Enter the specific port numbers or range of ports then click “Next”.
Choose the action to take when the rule applies then click “Next”:
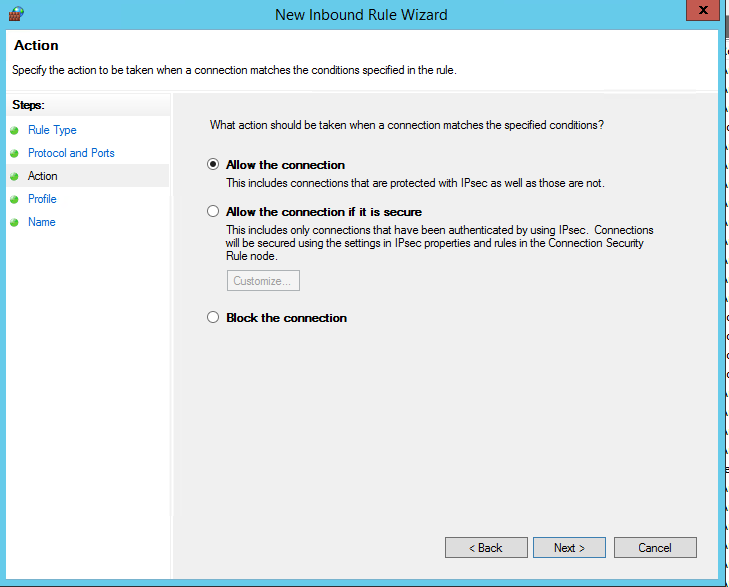
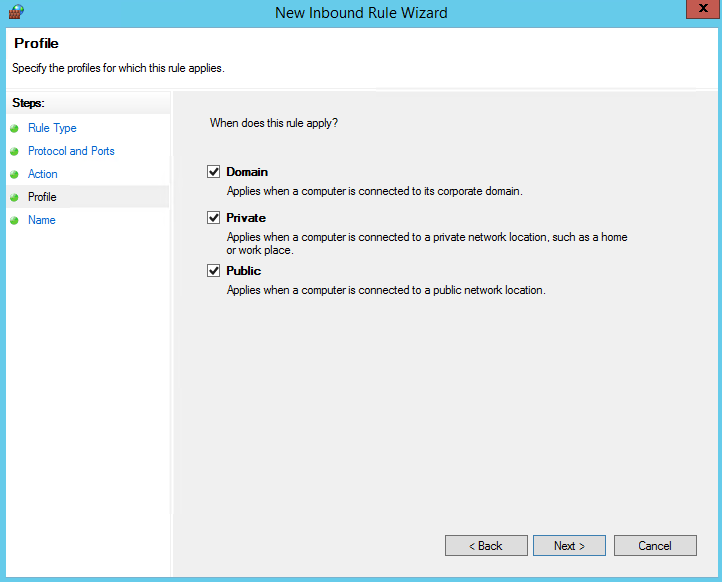
Choose the profiles to which the rule applies then click “Next”:
Provide a name and description for the rule. Click Finish.
Setup Firewall on Our Windows 2012 VPS Hosting!
Acquire a Windows 2012 VPS hosting server with the capacity for a next-generation, high-performance, enterprise-class infrastructure.
Outbound rules control the traffic that is allowed to leave the server. The process is similar to configuring inbound rules.
In the left pane, click on “Outbound Rules”. In the right pane, click on “New Rule….”. This opens the New Outbound Rule Wizard.
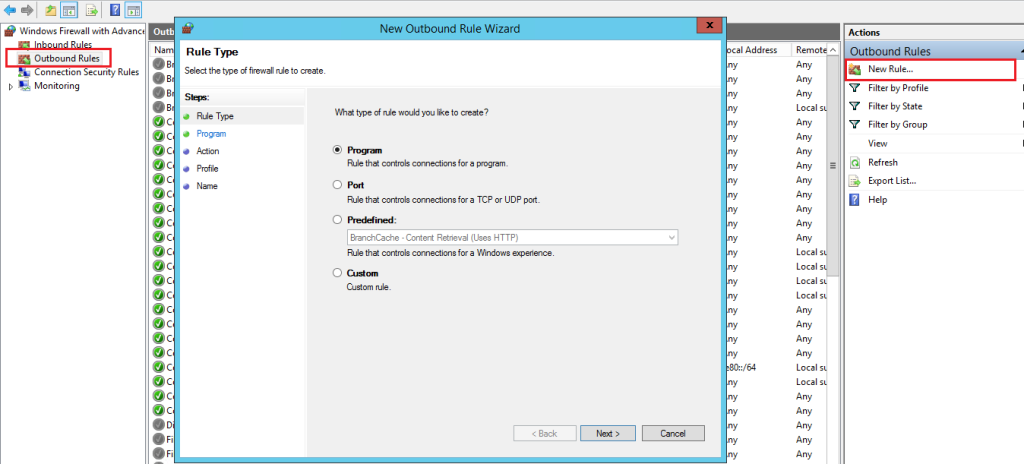
Follow the same steps as configuring inbound rules to create and customize the outbound rule.
Connection security rules are used to secure traffic between two devices.
In the left pane, click on “Connection Security Rules”. In the right pane, click on “New Rule….”. This opens the New Connection Security Rule Wizard.
Select the type of rule you want to create. Common types include:
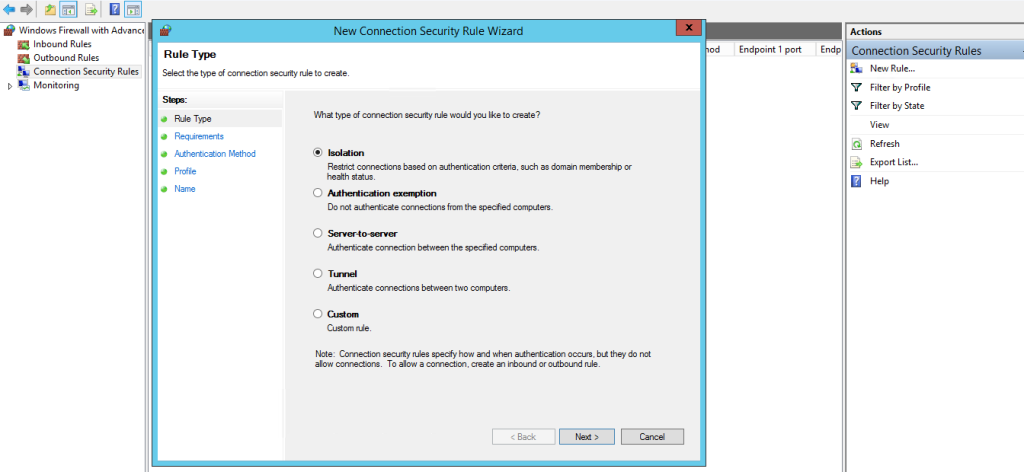
Follow the wizard to specify the authentication methods and endpoints. Click “Finish” to create the rule.
Once you have configured your rules, it is essential to monitor and manage them regularly.
To view a rule, select Inbound Rules or Outbound Rules in the left pane. Right-click on the rule and select Properties to modify it.
Right-click on a rule and select Enable Rule or Disable Rule. Right-click on a rule and select Delete.
The firewall can log dropped packets and successful connections. To enable logging, right-click on Windows Firewall with Advanced Security and select Properties. Configure the Logging section.
Learn about How to Open or Block Ports Using Windows Firewall.
Following are some best practices while setting up the Windows Server 2012 firewall configurations:
Configuring the Windows Server 2012 Firewall is an essential task for maintaining server security. By following the steps outlined in this guide, you can create and manage firewall rules that protect your server while allowing necessary traffic. Regularly review and update your firewall configuration to adapt to changing network requirements and security threats.
Streamline your Firewall setup on Windows with Ultahost’s secure VDS hosting, offering powerful processing, increased memory, and ample storage, Ultahost lets you focus on managing your projects effortlessly while delivering the performance and resources needed for smooth operations.
It is a security feature that controls network traffic to and from the server.
Go to the Control Panel, select “System and Security,” then click “Windows Firewall”.
Yes, you can create custom inbound and outbound rules to allow or block specific traffic.
Open Windows Firewall settings and turn it on for different network profiles.
Inbound rules control traffic entering the server, and outbound rules manage traffic leaving the server.
Use tools like ping or telnet to check the network connectivity based on your rules.
Proper configuration protects the server from unauthorized access and potential threats.