Installing and Securing phpMyAdmin on Ubuntu ...
Managing MySQL databases is a crucial part of web devel...
Authentication plays a pivotal role in upholding security within the digital realm. It encompasses the process of validating the identity of a user or system, thereby enabling access to specific resources or services. When it comes to remote access to servers, two primary authentication methods come to the fore: SSH key-based authentication and password-based authentication.
SSH key-based authentication offers a mechanism for logging into a remote system by employing a cryptographic key pair, replacing the conventional password approach. This key pair comprises a private key and a corresponding public key. The private key remains securely stored on the client-side, while the public key finds its place on the remote server. During a login attempt, the server verifies the client’s private key against the public key stored on its end.
On the other hand, password-based authentication relies on a combination of a username and password to authenticate the user. Prompted by the remote system, the user provides the designated username and associated password. Subsequently, the system undertakes a verification process to ascertain the correctness of the provided combination before granting access.
Both SSH key-based authentication and password-based authentication have their merits and considerations, and the choice between the two hinges upon the specific security requirements and user preferences.
SSH key-based authentication indeed offers a secure approach to authentication by eliminating the need to transmit passwords across the network. This enhanced security is achieved through the client-side retention of the private key, ensuring that it is never sent over the network. Consequently, SSH key-based authentication mitigates the risks associated with password interception.
Another notable advantage of SSH key-based authentication lies in its resistance to brute-force attacks, which are often employed to crack passwords. Since SSH key-based authentication relies on cryptographic key pairs rather than passwords, it significantly reduces the vulnerability to such attacks, bolstering overall security.
However, it is worth noting that SSH key-based authentication does have some drawbacks. One such drawback is the responsibility placed on users to manage and safeguard their private keys. Users must exercise caution and store their private keys in secure locations to prevent unauthorized access. Negligence in securing private keys could potentially compromise the authentication process.
Moreover, the initial setup of SSH key-based authentication can be more intricate compared to password-based authentication. This complexity may necessitate additional training and support to ensure proper configuration and usage. Despite these considerations, SSH key-based authentication remains a robust and widely adopted method due to its notable security advantages over password-based authentication.
Password-based authentication is indeed a widely employed method of authentication due to its simplicity and user-friendly nature. It offers convenience for users as it is relatively easy to set up and use, requiring only a username-password combination for access. Furthermore, users have the flexibility to create complex passwords, incorporating a variety of characters, numbers, and symbols, to bolster security. Regular password changes also contribute to strengthening overall security posture.
However, password-based authentication does have its drawbacks. One significant vulnerability is its susceptibility to brute-force attacks. These attacks involve automated tools or scripts attempting various password combinations until the correct one is found, potentially compromising the system’s security. The success of such attacks is amplified when users choose weak passwords that are easily guessable or commonly used, providing attackers with an advantage.
To mitigate the risks associated with password-based authentication, it is crucial to encourage users to adopt strong, unique passwords that are not easily guessable. Additionally, enforcing password complexity requirements, implementing account lockouts after multiple failed login attempts, and utilizing additional security measures such as two-factor authentication can help enhance the security of password-based authentication systems.
While password-based authentication remains a widely utilized method, it is essential to continually educate users about best practices for password management and promote the adoption of alternative authentication methods that offer increased security, such as SSH key-based authentication or biometric authentication, where applicable.
Indeed, SSH key-based authentication is generally regarded as a more secure method compared to password-based authentication. The key reason behind this lies in the fact that private keys are never transmitted over the network, minimizing the risk of interception. Consequently, SSH key-based authentication provides greater resistance against brute-force attacks, as there is no password to crack.
Password-based authentication, on the other hand, is more vulnerable to various attacks, including brute-force attacks where attackers systematically attempt multiple password combinations to gain unauthorized access. To enhance the security of password-based authentication, additional measures such as enforcing password policies (e.g., complexity requirements, password expiration) and implementing multi-factor authentication can be implemented.
In terms of ease of use, password-based authentication is generally more familiar and easier for users to set up and manage. Users are accustomed to the concept of usernames and passwords and often require minimal training or support. On the contrary, SSH key-based authentication may involve a learning curve and necessitate additional training and support, especially when it comes to generating, managing, and securing private keys.
While managing SSH key-based authentication can initially be more complex due to the need to handle private keys, once properly set up, it can provide easier management compared to password-based authentication. With SSH key-based authentication, users are relieved from the periodic task of managing and resetting passwords, contributing to a more streamlined and efficient authentication process.
Unlock the power of Ulta SSH VPS
Buy SSH Full Linux Root Virtual Private Servers with Instant Setup, Our VPS includes a free trial for 30 days, Choose different Linux-based operating systems.
To set up SSH key-based authentication, follow these steps:
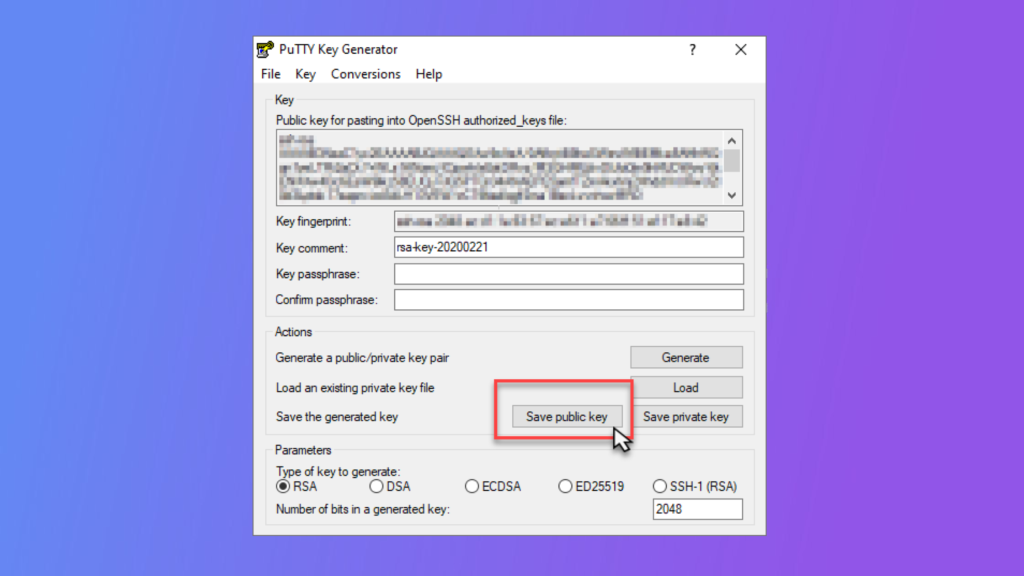
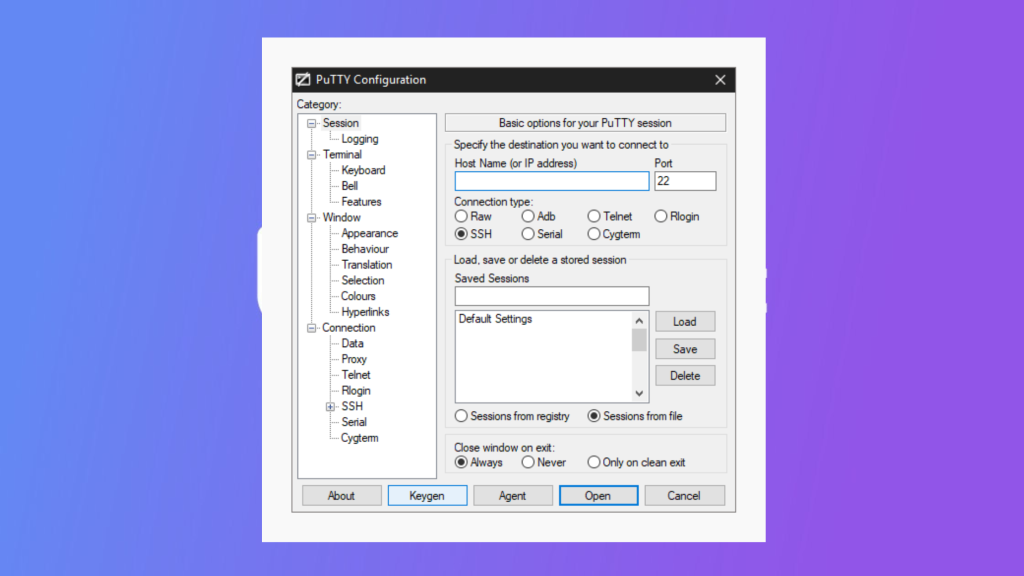
It’s important to keep in mind that managing SSH keys requires careful attention to security. You should store your private key in a secure location and protect it with a strong passphrase. Additionally, you should monitor your authorized_keys file on the remote server and remove any keys that are no longer needed.
To use an SSH key for authentication, follow these steps:
ssh -i ~/.ssh/id_rsa user@remote_server
It’s important to keep your private key secure and protected with a strong passphrase. Additionally, you should be careful when copying your public key to remote servers and only add it to servers that you trust. Finally, you should regularly monitor your authorized_keys file on remote servers and remove any keys that are no longer needed.
Best Practices for Authentication
Choosing the appropriate authentication method for your organization requires careful consideration of various factors. Security requirements, user needs, and the level of support and training required all play crucial roles in making an informed decision.
When it comes to password-based authentication, implementing a comprehensive password policy is essential. This policy should outline guidelines that encourage users to create strong, complex passwords, refrain from reusing passwords, and regularly change them. Additionally, educating users about password best practices, such as avoiding easily guessable information and using password management tools, can significantly enhance security. Multi-factor authentication (MFA) is another valuable measure to consider, as it adds an extra layer of security by requiring users to provide additional verification factors, such as a code from a mobile app or you can use your fingerprint scan.
For SSH key-based authentication, establishing an SSH key policy is vital for effective management and security. This policy should define the processes for generating, storing, and accessing private keys. It should address key rotation, revocation, and the procedures to follow in case of key loss or compromise. Providing clear guidelines on how to protect and securely store private keys is essential to prevent unauthorized access.
Furthermore, ongoing user education and awareness about the chosen authentication method, its benefits, and best practices for secure usage should be a part of your organization’s security culture. Regularly reviewing and updating authentication policies and procedures in response to evolving threats and security needs is also crucial to maintain a robust authentication system.
By carefully considering these factors and implementing appropriate policies and measures, you can establish a strong authentication framework that aligns with your organization’s security goals and effectively protects your resources and sensitive data.
Encountering an “SSH Connection Refused” error on your server can be a roadblock to remote access. Upgrading to an Ultahost Linux VPS server empowers you to diagnose and fix the issue effectively which grants you root access and full control over your server configuration. This allows you to verify if SSH is running, adjust firewall settings, or even reinstall SSH if necessary.
What is the difference between SSH key and password authentication?
SSH keys use cryptographic pairs for access, while passwords rely on user-entered credentials.
Which is more secure: SSH key or password authentication?
SSH key authentication is generally more secure and resistant to brute-force attacks.
Is SSH key authentication faster than password authentication?
Yes, SSH keys enable quicker logins as they avoid manual password entry.
Do SSH keys require a password to use?
Optionally, SSH keys can be protected with a passphrase for added security.
Can SSH keys be shared across systems?
Yes, public keys can be installed on multiple servers, enabling access from one private key.
Are passwords easier to manage than SSH keys?
Passwords are simpler but less scalable and harder to manage securely at scale.
Which method is recommended for automated scripts or deployments?
Passwords are simpler but less scalable and harder to manage securely at scale.