The popularity of WordPress has been steadily on the rise, and with that, the prevalence of attacks, viruses, and other threats has also increased. Criminals can create significant trouble for website owners and online merchants. This article will help you in securing WordPress website and protecting it from viruses.
Malware that targets WordPress-based websites actively searches for and exploits vulnerabilities, primarily found in plugins and themes. It then injects problematic or malicious code that can perform various tasks, depending on the type of virus.
Before I delve into securing WordPress against viruses, it’s crucial to understand the potential risks you may encounter.
Viruses and WordPress Websites
Many consider WordPress itself a highly secure platform. With developers worldwide continuously working on its improvement, vulnerabilities are quickly identified and patched.
However, despite its secure reputation, why do viruses often target WordPress? The answer lies in its immense popularity as the most widely used content management system, powering around 40% of all websites globally. Its widespread use also makes it a prime target for attacks.
The inherent nature of WordPress itself contributes significantly to its security challenges. From the outset, developers design it as a modular and user-friendly platform. Its biggest advantage lies in enabling the creation of professional and sophisticated websites without requiring expertise in HTML, CSS, or PHP. This convenience is made possible by the extensive use of plugins that add various functionalities.
Themes and plugins pose an additional potential weak point for WordPress security, especially when they come from less experienced companies or regular users. Code errors and inconsistencies in these plugins can serve as an open invitation to cyber threats.
Even the most robust security measures, including firewalls, antiviruses, two-factors authentication, greylists, and proactive monitoring might not be sufficient to stop a determined attacker.
Furthermore, the risk increases when an inexperienced individual is responsible for managing the website – a scenario frequently associated with WordPress’s user-friendliness. Such individuals can unknowingly make significant mistakes that leave the WordPress site vulnerable, rendering even the most secure WordPress hosting services ineffective in ensuring complete protection.
How to Verify if My Website Is Infected?

Before you proceed with securing WordPress website, it’s essential to check if unauthorized access has already occurred.
- Visit your website and explore different products, categories, and offers. Add items to your cart and proceed to the payment module. If everything goes smoothly without any unusual incidents, like pop-ups or sudden redirection to unrelated pages, your website appears to be in good condition.
- Utilize FTP to browse through folders and search for files with random names, such as “46fr1s55p9_index.php”, “cl03haxmng_index.php”, or “q9z91fmzq6_index.php”, or any other similar styles.
- Check main files like index.php, wp-config.php, and wp-settings.php for any presence of malicious code. To do this effectively, enable the display of spaces and tabs in your file editor. Look at the screenshot provided below. Initially, it may seem like a standard WordPress file, but pay attention to the gray dots indicating an excessive number of spaces.
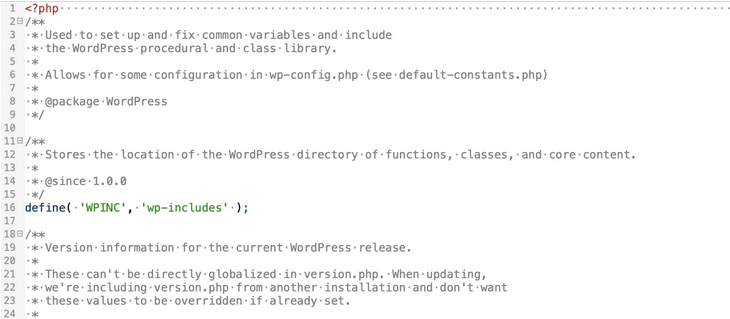
- Scroll the window to the right or enable line wrapping to unveil any hidden malicious code, as shown in the example.
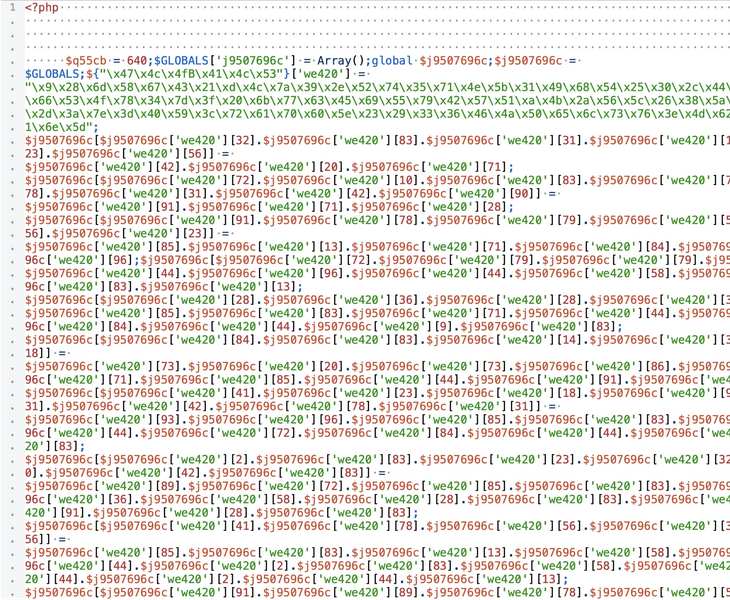
- Take a thorough approach when examining all WordPress files on your website, especially PHP files, as malicious code could be concealed in different parts of your site.
- Check the organic search results on Google by entering: site:your-domain.com. If your website is infected, Google might display numerous irrelevant results promoting casinos, gambling games, applications, and even illegal content like pornography or weapon sales.
- To enhance your website’s security, consider installing a malware search program, such as WebDefender Security – Protection & AntiSpam. This plugin allows you to search for any hidden viruses on your website.
However, each identified issue requires individual examination and verification to determine if it constitutes malicious software. Some plugins we use may contain code that could be classified as malicious, which is not uncommon.
How to Protect WordPress from Viruses?
Here is a list of proactive steps that undoubtedly create obstacles for cybercriminals and minimize the risk of your website falling victim to a virus. However, it’s crucial to acknowledge that these suggestions might not provide complete protection, depending on the virus type or attacking bots. Antivirus and virus developers engage in a constant arms race.
Whenever a new form of attack or virus emerges, antivirus creators strive to promptly neutralize it. Similarly, security measures are continuously updated, but eventually, criminals find ways to bypass them. Thus, achieving absolute immunity against viruses remains unattainable, but you can significantly lower the risk of infection.
Hosting
Selecting the right hosting provider is a critical aspect of any website. Many website owners often base their decision on prices or recommendations from others. However, it’s not that straightforward. First and foremost, you should verify if the hosting provider:
- Has the latest PHP version – currently 8.2,
- Performs regular backups of the database and files, and whether you have easy access to them,
- Offers protection against DDoS attacks.
Besides security considerations, it’s also essential to check the server’s parameters (processor, RAM, storage capacity, limits) provided by the hosting company.
Opting for UltaHost, which prioritizes security, is a wise choice. It goes beyond implementing multi-layered security systems across various infrastructure levels. UltaHost independently constructs data centers worldwide to maintain complete control over the quality of services offered.
This approach ensures the use of high-quality components not only in servers but throughout the entire infrastructure. Moreover, UltaHost’s data centers adhere to strict security standards set by the European Union. With UltaHost, you can have complete confidence in the security of your data and websites.
SSL Certificate
An SSL certificate encrypts all the information exchanged between the user’s browser and the website. Every reputable hosting company offers both paid and free SSL certificates (e.g., Let’s Encrypt) as part of their packages. You can find more information on this topic in this article:
WordPress Updates
Regular WP updates not only introduce a variety of new features and possibilities but also include crucial security fixes. It’s equally important to keep your plugins updated. Plugins and themes are particularly susceptible to virus attacks, so ensuring they are always up-to-date is essential to minimize risks.
Even if you’re not actively using them and they are deactivated, they can still serve as an entry point for cybercriminals. Hence, it’s vital to update all installed plugins on your WordPress site.
Uninstall Unnecessary Plugins and Themes
Following the same principle, it’s better to uninstall unused plugins or themes rather than just deactivating them. It is the recommended approach. Even if you occasionally require a specific plugin, uninstall it once you are done using it.
Reinstalling it will only take a few moments. It’s not worth risking potential attacks on your site just to save two minutes per month. Likewise, if you have multiple installed themes, uninstall all of them except the one currently in use. Only the active theme is necessary for your site, while the rest can act as gateways for cybercriminals.
Minimizing risks wherever possible is crucial. Don’t make it easier for hackers and malicious bots!
Hiding WordPress Version and Plugins
By default, WordPress shows the installed version in the page source by adding a tag in the HEAD section:
<meta name=”generator” content=”WordPress 5.6.4″ />
For WordPress plugins, it adds ?ver=X.X to the CSS and JS file URLs.
Revealing the versions of the components we use on our site makes it easier for attackers to target us, as they become aware of vulnerabilities specific to each software version.

To block the display of version information, we can add the following code to the functions.php file in our template:
remove_action(‘wp_head’, ‘wp_generator’);
add_filter(‘the_generator’, ‘__return_empty_string’);
function shapeSpace_remove_version_scripts_styles($src) {
if (strpos($src, ‘ver=’)) {
$src = remove_query_arg(‘ver’, $src);
}
return $src;
}
add_filter(‘style_loader_src’, ‘shapeSpace_remove_version_scripts_styles’, 9999);
add_filter(‘script_loader_src’, ‘shapeSpace_remove_version_scripts_styles’, 9999);
Regular Password Changes
Changing passwords for all site administrators every few months or even more frequently is a good practice, especially if your username is adm, admin, administrator, or domain name.
Changing the Administrator Login
Concerning the previous point, if your username is adm, admin, administrator, or domain name, it’s best to change it as soon as possible. The most commonly chosen username is admin, and changing it will limit the possibility of brute-force attacks on your site. Using one of the most popular usernames makes it easier for cybercriminals to target your site.
How to Change the Login in WordPress?
Method I:
- Log in to the database through phpMyAdmin.
- Look for the wp_users table.
- Find your account and click edit.
- In the user_login column, change the old username to the new one.
Method II:
- In the WP panel, add a new user with Administrator privileges.
- Log in to the new account.
- Delete the old account.
Changing the Login Page
By default, you can access every WordPress site through URLs like:
example.com/wp-login.php,
example.com/wp-admin/
To reduce the number of brute-force attacks, you can use the Limit Login Attempts plugin to limit the number of login attempts and block a user for a specified time. However, if you want to fully secure the login form, you can change its location using the WPS Hide Login plugin.
It will be much harder to guess that the dashboard is located at
example.com/niceteddybear.
Blocking Access to Files
By using specific rules in the .htaccess file, you can secure external access to particular files or folders.
In the main WP folder, you’ll find the xmlrpc.php and wp-config.php files, which store data for the MySQL database. Therefore, it’s recommended to add an extra layer of security for these files by adding the following rule to the .htaccess file located in the same folder.
<files wp-config.php>
order allow,deny
deny from all
</files>
<files xmlrpc.php>
order allow,deny
deny from all
</files>
Furthermore, in the /wp-content/uploads/ directory, if it doesn’t exist, create a .htaccess file and add the following rule to block the execution of certain viruses:
<Files ~ “.ph(?:p[345]?|t|tml)$”>
deny from all
</Files>
Disabling Unnecessary Functionalities
WordPress provides various functionalities that are often unused, making it worthwhile to disable some of them. If you use comments, consider disabling the first two checkboxes in Settings → Discussion.
Pingbacks serve the purpose of informing the site administrator when someone links to their post. If you don’t utilize built-in WordPress comments, install the Disable Comments plugin.
Security Plugins
As new attacks and viruses targeting WordPress-based websites keep emerging, many companies have introduced add-ons to help us defend against them. Some examples of these plugins are Wordfence Security, All In One WP Security & Firewall, and iThemes Security.
These plugins mainly focus on ensuring the security of our websites by detecting malicious software and blocking brute-force attacks. However, it’s worth noting that using these plugins may lead to a slight decrease in website speed.
Backup Copies
Creating regular backup copies is crucial, even if your hosting provider already handles it for you – just like UltaHost, which automatically performs daily backups of your WordPress Hosting.
Being cautious means being extra secure, so it’s still recommended to take care of your backup copies, especially before and after making significant changes to your website, even if you trust your hosting provider.
WordPress offers numerous backup plugins, but one worth recommending is UpdraftPlus. This plugin enables automatic backups that can be sent to another server.
Conclusion
Securing your WordPress website against viruses is of utmost importance in today’s digital landscape. With the increasing popularity of WordPress, the risk of attacks, viruses, and other threats has also risen significantly. Cybercriminals can cause substantial damage to website owners and online businesses if not properly protected.
By following these recommendations, you can significantly reduce the risk of your WordPress website falling victim to cyberattacks. Remember that maintaining a proactive approach to security and staying informed about the latest threats will contribute to a more robust and secure WordPress experience. Stay vigilant, and continue to prioritize the protection of your valuable online assets.
Are you worried that you have to pay extra for our secure hosting platform? Don’t worry, it is not only secure but also cheap WordPress Hosting! Get 24/7 support from our support team. Our powered infrastructure focuses on auto-scaling, performance, and security. Let us show you the difference! Check out our WordPress Hosting plans!