DDoS attacks are one of the biggest threats on the Internet. Don’t be fooled by the attacks most covered by the media. You must be aware that not only large corporations or government institutions are in danger. Your business website is also at risk. Botnet networks perform 98% of DDoS attacks targeting small and medium websites. To protect your business, you need DDoS-Protected VPS. How does it work?
Is it possible to stop or mitigate DDoS attacks?
The issue of protection against DDoS attacks is quite complex. These attacks are simple: they bring so much traffic to a website that it becomes impossible to function. Therefore, they try to occupy the VPS hosting bandwidth.
Types of DDoS attacks
You can read about the details of DDoS attacks in another article on our blog, so I won’t go deep into describing the basics of Distributed Denial of Service attacks here. I will focus on DDoS protection and DDoS mitigation solutions.
Firstly, there are two main types of attacks: volumetric attacks and application layer attacks, also known as protocol attacks.
Volumetric floods involve sending an immense amount of requests to clog the server. All hosting services have the bandwidth and computational limitations. If the number of requests exceeds the server’s capabilities, it will not be able to respond to subsequent requests, causing the website to either stop working or operate sluggishly. The majority are SYN floods.
DDoS aims not only at websites, but any Internet-connected services, such as chat services, social media platforms, banking services, mobile applications, or game servers. The second type of attack is slightly more complex and involves sending smaller data packets to the server over a long period, which also ultimately affects the server’s security and its ability to respond to new requests.
If you want to know more details about what Distribution Denial of Service is, read this article:
Stopping a DDoS attack
Stopping a DDoS attack is easier when it comes to volumetric attacks. In theory, blocking traffic from specific locations at the time of the attack or utilizing various cloud services, such as a content delivery network, is sufficient. However, defending against protocol attacks is more challenging.
In practice, when a DDoS attack on your website or application has already started, there may not be much you can do, especially if it’s a strong attack carried out by an organization with significant resources. Only the best DDoS-Protected VPS hosting services with sophisticated protection systems can save you.
To achieve this, DDoS-protected VPS would need to combine early detection, blocking traffic from the most active regions during an attack, utilizing CDN networks, and additional automatic traffic recognition techniques. All of these actions would need to be interconnected and integrated. It is easier to mitigate attacks.
Mitigating DDoS Attacks
To mitigate attacks, you need to understand the initial stage of their execution. Botnet networks scour the Internet to find the best targets. Criminals don’t commit these crimes just for fun; they want to gain specific benefits. Most often, they seek out victims who will be able to pay some ransom.
On the other hand, they search for easy targets that are poorly secured or have insufficient or outdated protections. Cybercriminals don’t want to engage in an epic battle with a solid DDoS-Protected VPS just to prove they can break it. They want an easy target that won’t put up too much resistance.
To mitigate DDoS attacks, use a DDoS-Protected VPS service that will prevent botnets from targeting your site. What should characterize this type of Virtual Private Server? Bot protection system should be clear and visible at first glance. The more security systems DDoS-Protected VPS hosting has and the more visible they are, the less likely a botnet will target your site.
How does DDoS protection work?
DDoS protection works in various ways. On the one hand, DDoS-Protected VPS must deter botnets from searching for victims. Neither you nor cybercriminals want the botnet to target your DDoS-Protected VPS services.

Mitigation at the early preparation stage
The first layer of DDoS protection is a system for the early detection of suspicious traffic. However, you can’t prevent a botnet from accessing your site because it is difficult to distinguish it from a user who wants to use your services or a bot with friendly intentions – for example, for a search engine or directory positioning.
Many bots have no impact on your site – either positive or negative. These are bots from external companies that are engaged in some form of Internet analysis or monitoring. Therefore, you cannot categorically block bot access to your site.
You can, however, use a system that can detect suspicious traffic, matching the pattern of the preparatory phase of an attack. The botnet first sends a scout that registers thousands of pages that can be attacked and then sends a group of bots to test DDoS protection systems.
It is the moment when you can effectively mitigate the attack with an advanced anti-DDoS solution that can detect such suspicious traffic. The botnet will abandon the attack if your Web Application Firewall disables 5 out of 20 bots. Another example of action at this stage is adding compromised IP addresses to a blocklist.
Traffic dispersion across different servers
Another way of DDoS protection is to disperse traffic across other servers. It is how a Content Delivery Network works. CDN servers copy your site’s static content and load it from the distributed network.
CDN is effective against the simplest attacks and most common attacks. However, a better-organized Distributed Denial of Services will bypass a CDN by focusing on dynamic data.
To this end, some DDoS protection systems create an internal network similar to CDN but based on dynamic data and only launched when a DDoS is registered. It involves copying dynamic content to several different servers at that time, making it harder to block them.
Traffic blocking and routing system
An intelligent system can detect DDoS attack patterns as they begin and take appropriate steps. It may include blocking traffic from certain countries and introducing temporary restrictions for automated systems in accessing the site. Some malicious traffic can also be routed to other servers to filter it from legitimate traffic.
Best DDoS-Protected VPS Hosting
VPS hosting is vulnerable to DDoS attacks because they have dedicated resources for a given user. So, for example, a given site has access to a virtual machine with 8 GB of RAM and 4 processor cores. It is easier to block such a site than another one operating on a shared server that has no dedicated resources.
A virtual hosting provider may also put less effort into their DDoS protection. In the case of shared hosting, the hosting provider suffers the most during the attack because it hits the entire server, causing damage to all clients. Therefore, hosting providers must protect themselves against DDoS attacks.
However, on a virtual server, only one client will be affected. When looking for a hosting provider, you need to look for one who prioritizes security issues and does not try to save money on security.

Therefore, the Best DDoS-Protected VPS Hosting will be better protected than shared hosting because these are clients who are particularly vulnerable to attacks carried out by botnets. Shared server clients are usually small, often amateurish websites. They do not have the resources to pay a ransom or a bribe.
VPS hosting is for entrepreneurs and companies – and they will be more willing to pay to stop attacks.
Best DDoS-Protected VPS will therefore have all possible DDoS-mitigation levels at the server entry and primary system, which other types of hosting lack. Additionally, root access enables the user to install an additional layer of security measures.
How does UltaHost protect its servers against DDoS attacks?
UltaHost places security as its top priority. Understanding that DDoS attacks pose one of the greatest threats on the Internet, alongside Malware and Viruses, UltaHost has optimized its defense systems specifically in this direction. This way, UltaHost clients can enjoy one of the safest DDoS-protected VPS services on the market.
Highest-quality hardware and software
The first layer of VPS DDoS protection is ensuring the latest hardware and other components. UltaHost invests in the latest Intel Xeon processors, high-quality NVMe SSD disks, and efficient RAM modules. Each server component, from cables to power supplies and motherboards, is sourced from reputable manufacturers.
This way, UltaHost can operate on a stable, efficient, and secure infrastructure that minimizes the risk of failures and security vulnerabilities. The company applies a similar approach to the software without compromising quality to maintain reliability.
BitNinja
For this reason, UltaHost’s primary security system is BitNinja. It is one of the most advanced solutions in terms of server protection platforms. It is based on automated, intelligent learning through a secure network. BitNinja systems are interconnected and exchange information in real-time.
BitNinja is a sophisticated system that protects against numerous malware threats, cyber-attacks, and various DDoS types. When there is a breach in any security area, the system immediately seeks solutions to the problem and notifies the central server. When the threat is neutralized, procedures of other BitNinja instances are updated to protect against new threats.
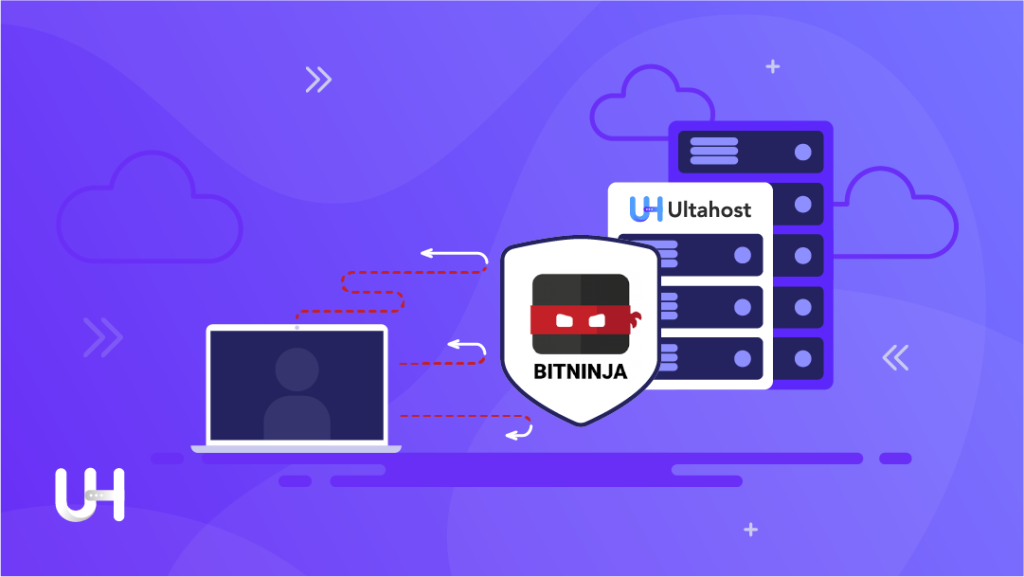
In this way, each breach of BitNinja’s defense on one server makes the entire system resistant to that threat. BitNinja has various modules, including several dedicated to DDoS protection.
It protects against HTTP Floods focusing on botnet mitigation and deterrence and tries to make network adjustments as quickly as possible during an attack to minimize its effects. BitNinja anti-DDoS module has different protection methods for UDP floods and SYN Flood attacks.
The basis of BitNinja protection is detecting suspicious behavior on DDoS-protected VPS servers in real-time and managing multi-level black and gray lists. In this way, different botnets are intercepted and identified, and DDoS-protected VPS servers by BitNinja become invisible to them.
Bad Traffic Redirecting
However, BitNinja is not the only security system used by UltaHost on DDoS-Protected VPS hosting. UltaHost also utilizes other systems for proactive monitoring, detecting, and identifying attacks. After detection, the systems initiate procedures to redirect the malicious traffic to scrubbing centers and servers specially designed for this purpose.
In this way, the botnet thinks that attack aims at the selected web server, engaging its resources, but the actual DDoS is redirected to a server specifically designated for this purpose. In particular cases, short and targeted blackholing may be applied to traffic from specific countries.
Cloudflare Content Delivery Network
UltaHost also uses one of the most renowned methods of anti-DDoS hosting solutions which is the Cloudflare CDN network. Cloudflare software detects DDoS attacks and activates limits that restrict bots and spammers’ access to the attacked servers. It relieves the server and enables real users to access the services.
Cloudflare’s firewall operation is fast because the service has over 165 data centers distributed around the world, so it responds from the nearest data center to the user visiting the website.
If you want to know more about the Content Delivery Network, read our other article on what is CDN.
Through continuous monitoring, Cloudflare checks who is trying to access the site (client, bot, or spammer) and takes appropriate action. Most botnets avoid websites and web applications protected by CDNs, especially Cloudflare’s CDN.
Each UltaHost’s VPS plan consists of free CDN Cloudflare DDoS protection.
Conclusion
Protection against DDoS attacks is crucial from a business standpoint. Blocking services for hours or even days could cause colossal losses for a company, which is why UltaHost focuses on providing effective protection to its servers against this threat.
The foundation is the BitNinja system, internal redirection systems, and Cloudflare’s CDN network. In this way, most DDoS attacks are mitigated and neutralized from the beginning. Botnet networks that are searching for targets typically bypass UltaHost’s servers, considering them too well-protected.
Of course, some are small targeted attacks paid for by your competition. In this case, deterrence does not work and protective systems must be used in practice. However, UltaHost is ready at all times, providing real-time free DDoS protection everywhere.
DDoS protection systems will provide your Virtual Private Server with security in the case of 99.99% of attacks, which is one of the highest VPS DDoS protection rates on the market.
UltaHost provides you not only DDoS protection. With your fully managed VPS, you will get dedicated IP addresses, an SSL certificate, incredible network capacity, two-factor authentication, automated backups, and automatic updates.
UltaHost provides you not only DDoS protection. With your fully managed SSH VPS, you will get dedicated IP addresses, an SSL certificate, incredible network capacity, two-factor authentication, automated backups, and automatic updates. Let us show you the difference! Check out our plans!