How to Install Chocolatey on Windows 10
Chocolatey is a package manager for Windows 10 that sim...
Imagine you’re playing your favorite online game, but you’re experiencing lag and connection issues. Or perhaps you’re concerned about the security of your Windows system and want to ensure no unauthorized access points exist. The culprit behind these scenarios could be open ports on your system.
Open ports act as virtual doorways that allow your computer to communicate with other devices or servers across a network. They play a crucial role in facilitating various online activities, from web browsing and email to file sharing and online gaming. However, open ports can also pose security risks if not properly managed, potentially allowing malicious actors to gain access to your system.
Understanding how to check open ports Windows is essential for both troubleshooting network problems and maintaining optimal system security. This process, known as port scanning, allows you to identify which ports are open, the services or applications associated with them, and potential vulnerabilities that may need addressing. The article will guide you on how you can check Windows open ports.
Open ports are TCP (Transmission Control Protocol) or UDP (User Datagram Protocol) ports that are currently in use by a running process or service on your system. These ports are essential for network communication protocols, as they allow different applications and services to exchange data. For example, when you access a website, your web browser uses port 80 (HTTP) or port 443 (HTTPS) to communicate with the web server.
There are 65,535 available TCP and UDP ports, divided into three ranges:
Explore the Blazing Fast Speed with Cheap Windows VPS!
With Ultahost, Hosting Windows VPS has never been easier or faster. Enjoy ultra-fast SSD NVME speeds with no dropouts and slowdowns.
Checking open ports is crucial for maintaining system security and preventing unauthorized access. Here are some reasons why:
Windows provides two built-in tools for port scanning: Netstat and PowerShell. Below we outline the basic guide on how to see open ports Windows.
Netstat is a command-line utility that displays active network connections, routing tables, and interface statistics. To use netstat for port scanning, you need to open Command Prompt as an administrator use the following command and press Enter:
netstat -an
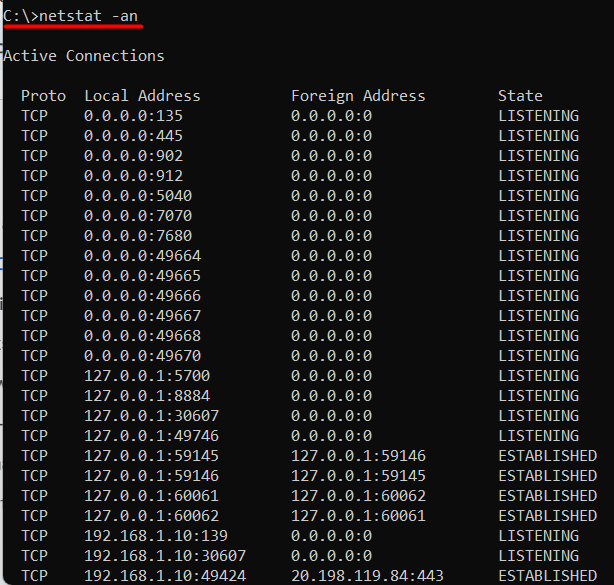
The -an option displays all active connections, including listening ports. Look for the “Local Address” column, which shows the IP address and port number of each connection.
PowerShell is a powerful task automation and configuration management framework from Microsoft. To use PowerShell for port scanning, you need to open it as an administrator and then execute the below command:
Get-NetTCPConnection
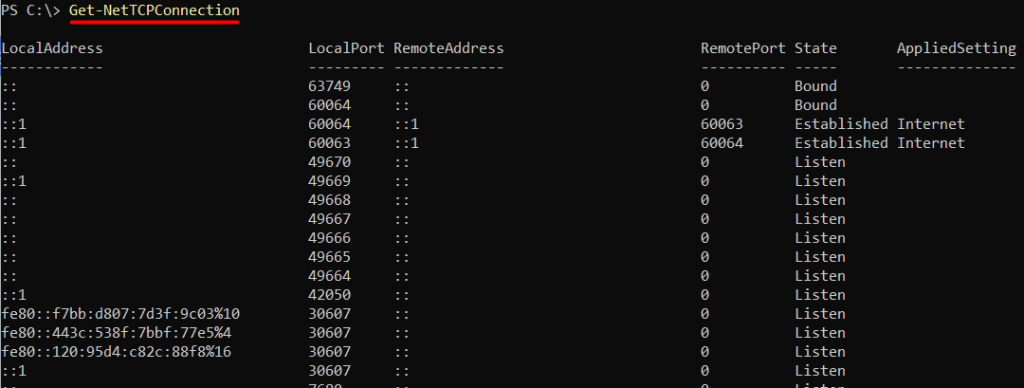
This cmdlet displays all list open ports Windows, including listening ports. Look for the “LocalAddress” property, which shows the IP address and port number of each connection.
While built-in tools can provide basic port scanning capabilities, third-party software offers more advanced features and flexibility.
Nmap is a popular, open-source port scanner that provides detailed information about network hosts and services. To use Nmap:
Download and install Nmap from the official website.
After installing it you need to open the open Command Prompt as an administrator and execute the below command:
Type nmap -p 1-65535 <IP address>
Replace <IP address> with the IP address of your system or a specific host. Nmap will scan all 65,535 ports and display the results, including open ports and services:
nmap -p 1-65535 192.168.10.1
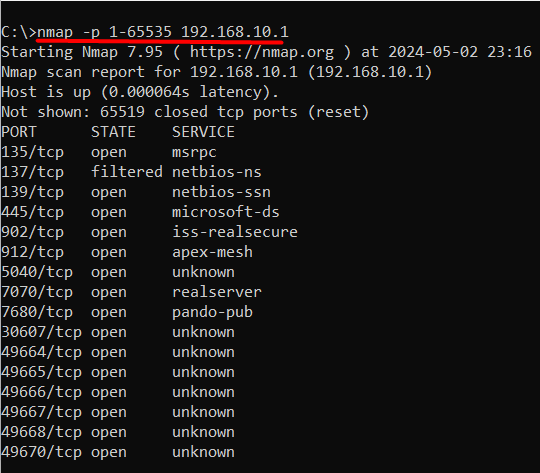
If you are unaware of your IP address then you can execute the ipconfig command on the command prompt to find it.
For more detailed instructions refer to our guide How to install Nmap on Windows.
Open ports play a vital role in facilitating online activities, but they can also pose significant security risks if not properly managed. Understanding how to check open ports in Windows is essential for both troubleshooting network problems and maintaining optimal system security. By identifying open ports, users can determine which services or applications are associated with them and address potential vulnerabilities that may need attention.
By utilizing built-in tools like Netstat and PowerShell, or third-party software like Nmap, users can effectively scan for open ports and take necessary steps to ensure system security. Regular port scanning can help prevent malware infections, unauthorized access, and resource utilization, ultimately protecting sensitive data and system integrity. By grasping the importance of open ports and how to manage them, users can take a proactive approach to maintaining a secure and efficient Windows system.
While enabling open ports on your Windows machine can be useful for specific applications but it also introduces security risks. For a more secure and controlled environment rent a VPS from Ultahost. These VPS plans grant you root access and complete control over your server’s firewall configuration. This allows you to open ports with specific control ensuring only necessary ports are exposed.
Open ports are communication endpoints that allow data to be transmitted between a device and a network. In Windows, these ports can be in a listening state, waiting for incoming connections, or actively transmitting data.
Checking open ports can help you identify any potential security vulnerabilities on your Windows system. Unnecessary open ports could be exploited by malicious actors to gain unauthorized access to your system or to launch attacks.
You can check open ports in Windows using various methods, including using built-in command-line tools like Netstat or PowerShell, third-party software, or online port scanning tools.
To use the netstat command, open Command Prompt, and type netstat -an. This will display a list of all open ports and their respective states (listening, established, etc.).
Yes, PowerShell provides cmdlets such as Get-NetTCPConnection and Get-NetUDPEndpoint that allow you to check open TCP and UDP ports, respectively.