How to Install Tutor LMS in WordPress
Tutor LMS is a Learning Management System plugin in Wor...
Contact form spam is defined as unrequested or automated submissions sent through website forms. These submissions typically include irrelevant links, phony queries, or promotional information produced by bots. Contact form spam can clutter your inbox, cost you valuable time, and can increase your chances of receiving phishing and malware, as long as they are not blocked.
Having an unprotected contact form harms user experience. A legitimate visitor may receive slow responses or no responses at all because of the overload of spam submissions. Spam submissions can also hurt a server’s performance and create distrust in a website.
Securing your contact form will reduce the chance of your contact form spam submissions and will also protect users’ data and help ensure effective communication. Good contact form spam prevention security will also bolster your website’s performance and maintain a cleaner communication line. Less spam submissions mean a better experience for your customers and a better online reputation.
The rest of this article will go through all the proven ways to secure your contact forms, lower your spam submissions, and protect your website from automated attacks.
Experience UltaHost’s Secure WordPress Hosting!
Enjoy peace of mind with UltaHost’s secure WordPress servers, offering 24/7/365 protection against DDoS attacks, malicious traffic, and malware
Forms are typically left open to exploitation. This usually means that spammers are able to access any form on your site, fill it with vast amounts of junk, and spam you without you even knowing they’ve done it. Spams are automated programs that visit web servers, locate forms, or look for exposed forms, and send junk content through the forms en masse.
Spammers are able to submit forms in order to add links placed within your form submissions that are linked to pages that may or may not be phishing pages. After clicking these links, the user is tricked into entering their passwords or personal data. Sometimes spam submissions contain malware payloads which will compromise security gears on your site if users click on the links during a form submission. Making the humble form a significant risk vector.
Most spammers will scrape forms which ask for account email address, phone numbers, and names, and use this data to build email lists or targeted email campaigns. Not only does this exploit the account holder’s privacy, it exploits the brand name for possible spam campaigns as well.
Massive amounts of spam submissions will bottleneck your server and impact web speed and even search rank speed. A slow website usually equates to poor search ranks. A case could even be made that the links included in spam submissions through forms would warrant company or business blacklisting if search engines (Google) detect abnormal behavior logs associated with the links.
Every spam submission increases the risks that you overlook a legitimate customer inquiry. This directly impacts the business in degradation customer service ability and being delayed in responding to real sales/service requests.
CAPTCHA and Google reCAPTCHA function as a barrier against spam bots by verifying that a user is a distinct person. reCAPTCHA v2 requires users to complete a simple task such as checking a box, while v3 simply runs in the background evaluating a risk score on behalf of the user:
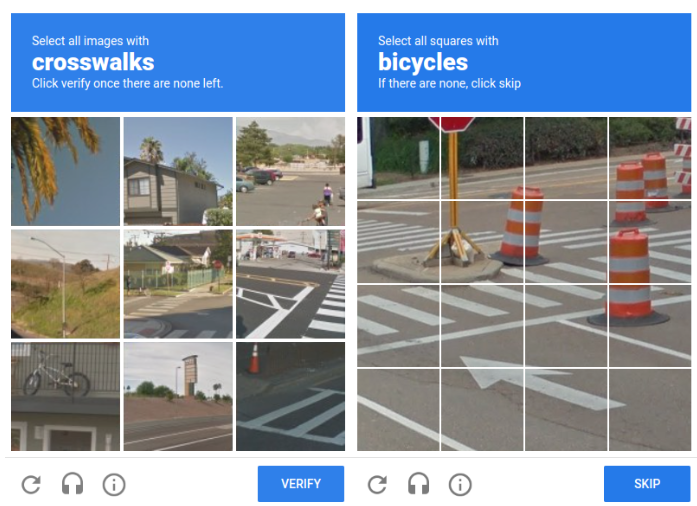
Using these tools, searches can tell non-human behavior apart from automated scripts, making it more difficult for bots to evade input verification when filling out forms. An important line of defense is implementing CAPTCHAs, read our guide about How to Generate Google reCAPTCHA Keys for Site Security.
CAPTCHA substitutes are available which offer the same bot detection and require little user interaction. Honeypot fields are hidden from users but visible to bots. When a bot fills out these then they are flagged automatically.
Honeypots work unobtrusively as they do not take away from usability. Simply take a hidden field, and when the form is submitted, check to see if something was entered. If the hidden field has any value on it then you know it’s spam. The Honeypot is an invisible spam trap and is a very convincing passive function.
Double opt-in refers to a process that requires the users to respond to a confirmation sent to them via email. The form will not process until the user clicks a link in the verification message. By activating double opt-in you stop fake emails from completing the form and strip out bots that use random and disposable email addresses. The email double opt-in feature is priceless for instances of a contact form or subscription form where valid user participation is being sought.
By adding restrictions to how often a form can be submitted, you can help protect against spam attacks. Some plugins and custom scripts allow you to set rules, such as allowing only one submission a minute. Form rate limiting stops bots from bombarding your inbox with spam and helps the server maintain stability during spam attacks.
Validation checks what a user is inputting is in the correct format, while sanitization removes harmful content. Both need to be performed server-side so that the malicious input is blocked before it enters your system. Protecting the form means rejecting anything that is not valid, and adding filtering of suspected malicious content, such as script tags or spam keywords, helps with securely accepting form submissions.
Blocking IPs is another way to stop spam, as most spam will come from the same IP. You can use systems such as Fail2Ban or Cloudflare that will help you keep IPs blocked (while filtering traffic out). Keeping IP blacklists updated can prevent spam in the future and help you to add that extra layer of firewall protection to your forms:
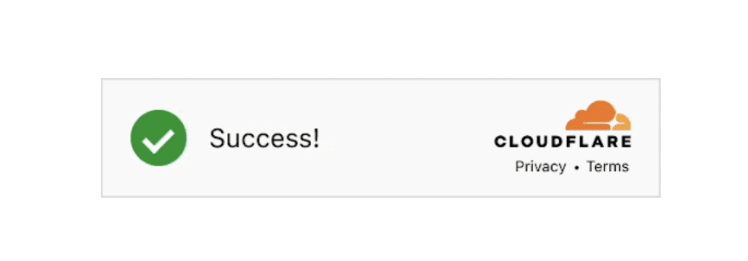
Learn also How to Install Cloudflare on Your WordPress Site.
Custom tokens (such as CSRF tokens) checks that a form was submitted by the user during a valid session and from your site. Every form will have its own unique token, so automation by bots will be more difficult. You can use PHP, JavaScript, or a wide variety of modern form plugins to conduct this implementation.
Filtering out temporary email providers like Mailinator can help to cut down on fake submissions. You can also filter based on trust or restricted domains too to make sure users are providing a genuine email. This is helpful in eliminating disposable email abuse through domain filtering and taking better submissions.
AI tools are another option to use like Akismet or OOPSpam. AI tools analyze behavior and the content of individual submissions. They look at input patterns, based on a pattern of events. Using AI spam detection adds a level of intelligent filtering and control beyond the generic spam detection.
This method only allows authenticated users to submit a form using a login system, making this implementable for member-only areas or internal forms. This should block most bots attempting form submissions, and also helps with verifying that the activity is traceable to a real user.
Choosing the right tools can bolster your form security and ease your management. In terms of WordPress sites, Akismet is a common choice for filtering spam using a database that’s constantly updated.

WPForms has many built-in inherent spam protection mechanisms such as smart CAPTCHA and honeypots. If you use Contact Form 7, you can enhance it by adding the Honeypot plugin-giving spam bots a silent trap at the front end of your contact form without disrupting the experience of a legitimate user:

Here are the details to Discover the Top 5 WordPress Anti-Spam Plugins for Protecting Your Website.
For wider use, Google reCAPTCHA is a good choice that works across platforms. Cloudflare also adds an additional layer of security by filtering spam on the DNS level and blocking known bot IPs:
OOPSpam is a solid entry as well, using AI to detect and stop spam in real time:

Overall, both form security tools and anti-spam plugins provide ways to customize spam protection for most types of website builds. The best course of action is to use more than one as a way to add layers of protection and help cover the various attack types.
To safeguard your contact forms, a proactive approach with layered defense is the best course of action. Employing CAPTCHA, honeypots, form tokens and rate limiting will easily keep bots from making it very far. In addition to those techniques, email verification, domain verification, and utilizing AI filters can be used to further protect your forms.
It’s important to remember to regularly monitor your forms, and run tests using tools like (OWASP ZAP), and always keep your anti-spam plugins updated. Nothing in this world can prevent or stop all spam and garbage in your forms, but if you’re able to combine multiple solutions together then your chances of stopping spam would be considerably increased.
To stop contact form spam and protect your user data, you should put these strategies into action on a continual basis. By securing your site against spam, you’ll not only be protecting it from spam – but you’ll be able to provide your users with a consistently clean and reliable experience while visiting your site.
When it comes to buying hosting Ultahost is the best place to provide WordPress VPS hosting for bloggers, business owners, web designers, and developers. A customizable and scalable VPS is made just for you.
Contact form spam refers to unwanted or automated messages submitted through web forms, often by bots. These messages usually include links, fake queries, or ads.
CAPTCHA checks if a user is human by asking them to complete a simple task. Bots usually fail these tests, blocking their submissions.
A honeypot field is a hidden input visible only to bots. If it’s filled out, the submission is flagged as spam.
It requires users to confirm their email via a link. This filters out bots and fake or temporary email addresses.
Rate limiting restricts how often a form can be submitted. This prevents bots from sending multiple spam entries in a short time.
Fail2Ban, Cloudflare, and similar tools can detect and block IPs known for spam. They add a protective firewall layer to your forms.
Yes, combining multiple spam prevention methods increases protection. Each technique blocks different spam behaviors.