What is SFTP Port Number?
With the world gradually becoming a "global village," t...
Telnet short for Telecommunication Network is a network protocol used on the internet or local area networks to provide a bidirectional interactive text-oriented communication facility using a virtual terminal connection. Despite being one of the oldest network protocols still in use it has largely been replaced by more secure alternatives like SSH for remote access. However, Telnet is still useful for testing and troubleshooting servers and network services.
In this guide, we will dive into the usage of the Telnet command Linux environments by providing you with knowledge on remote network connection.
After we discuss what is Telnet command it is important to understand its features and limitations:
Despite these limitations, Telnet can be useful for debugging or managing devices in a secure environment.
On most Linux distributions, the Telnet client is not installed by default due to its security issues. However, it can be easily installed using the package manager.
sudo apt-get update && sudo apt-get install telnet
sudo yum install telnet
sudo dnf install telnet
Setting Up the Telnet Command on Our Linux VPS today!
Ultahost provides Linux VPS hosting with NVME SSD storage. You can use telnet network protocol in our VPS to streamline your process.
The basic syntax for the Telnet command in Linux:
telnet [hostname/IP address] [port]
Replace hostname/IP address with the hostname or IP address of the device or service, you want to connect to and port with the port number of the service. Here’s an example of connecting to a remote machine on the default port:
telnet google.com 80
If successful you will see messages indicating an attempt to connect followed by a connection established notification. You might also see the escape character for the session often is ^.
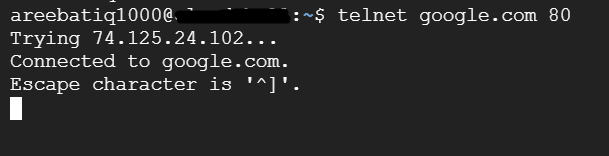
Once connected, you will likely be prompted for a username and password to log in to the remote machine. These credentials should match valid user accounts on the remote system.
After successful login, you will be in a remote shell environment. You can interact with the remote server using the standard shell commands available on that system.
To terminate the telnet session and return to your local machine type exit or quit at the remote shell prompt.
Following are some common examples of how to use telnet in Linux:
1. Checking Mail Services
You can test Google SMTP services running on a server using Telnet:
telnet smtp.gmail.com 25
After a successful connection, send an EHLO (preferred) or HELO command followed by your domain name. Press enter.
EHLO yourdomain.com
Use the MAIL FROM command to specify the sender’s email address. Then, use the RCPT TO command for each recipient’s email address. Press enter after each command.
MAIL FROM: [email protected] RCPT TO: [email protected]
Type DATA and press enter. This indicates you’re ready to send the email content. Type the email subject line on a new line. Press enter twice one blank line after the subject. Type the email body content. To finish, type a single period (.) on a new line by itself. Press enter.
DATA Subject: Test Email via Telnet This is a test email to verify SMTP connectivity. .
Type QUIT and press enter to disconnect from the SMTP server.
2. Testing HTTP Services
Test whether a web server is responding on port 80 to an HTTP or 443 HTTPS network protocol:
telnet www.website.com 80
A successful connection means the web server is listening on port 80.
3. Troubleshooting Other Services
Similarly, other services such as FTP on port 21 and SSH on port 22 or any custom application running on a specific port can be tested.
Because Telnet does not encrypt data, anyone who has access to a router, switch, or proxy along your connection path could potentially intercept your data. For sensitive tasks always prefer SSH or another secure method of communication. For those requiring secure communication consider using SSH which encrypts all traffic between the client and server. Other protocol-specific tools may also offer more robust options for testing particular kinds of applications; for example, using curl or wget for web services or openssl s_client for TLS/SSL secured services.
Telnet remains a valuable tool for networking professionals when dealing with non-critical data or within a secure environment. Its simplicity and wide availability make it useful for quick checks and troubleshooting network services. However, due to its lack of encryption and security features, its usage should be limited to scenarios where security is not a concern, or within isolated networks where traffic snooping is not a risk.
While the telnet command offers a basic way to connect to remote servers in Linux it transmits data unencrypted. This poses a security risk, especially for exchanging sensitive information. Upgrading to an Ultahost SSH VPS hosting provides a more secure and versatile solution that comes pre-configured for secure remote access using a secure shell that encrypts all communication between your device and the server.
Telnet allows you to connect to remote servers or devices over a network.
You can typically install Telnet using your package manager, like apt or yum.
Yes, Telnet can help diagnose network problems by testing connectivity to specific ports.
No, Telnet sends data in plain text making it insecure. Consider using SSH instead.
Yes, you can create scripts or use tools like expect to automate Telnet commands in Linux.