Iptables Firewall Essentials for VPS Protecti...
Iptables is a firewall utility that can be used to cont...
Nmap stands for Network Mapper is a free and open-source network detection and security scanning tool. It is used to discover hosts and services on a network, as well as to identify operating systems and open ports. Nmap can also be used to perform more advanced tasks, such as vulnerability scanning. Nmap can be downloaded in different operating systems such as Windows, macOS, and Linux platforms. If you have installed Kali Linux, Nmap comes pre-installed in the Kali operating system.
Nmap is a powerful network scanning tool that can be used to discover open ports and services on a target system, which includes systems protected by iptables firewall. However, the results of the scan will depend on the specific firewall rules that are in place. For example, if the firewall is configured to drop all incoming SYN packets, then Nmap will not be able to detect any open ports.
In this post, we provided you with a “Nmap cheat sheet of the essential commands and options.” This sheet is designed for network administrators, security professionals, and anyone else who needs to use Nmap to scan networks and systems.
The most basic Nmap scan is to scan all TCP ports on a single host. To do this, you can use the following command:
nmap <target_host>
Well in this case we need to assign the target host. For example, to scan all TCP ports on the host 192.168.1.1 you would use the following command:
nmap 192.168.1.1
This scan will return a list of all open ports on the target host, as well as the services running on those ports. For example:
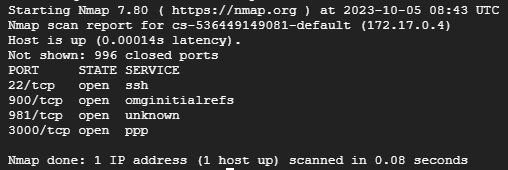
As the above screenshot shows the Nmap resulted in open ports such as SSH showing its ports and state.
Nmap can scan a single host, a range of hosts, or a list of hosts. To specify a target, use the -T option. For example, to scan the host 192.168.1.1, you would use the following command:
nmap -T 192.168.1.1
To scan a range of hosts, use the -R option. For example, to scan all hosts in the 192.168.1.0/24 subnet, you would use the following command:
nmap -R 192.168.1.0/24
To scan a list of hosts, use the -iL option. For example, to scan the multiple hosts and save all the hosts in the file hosts.txt, you would use the following command:
nmap -iL hosts.txt
Nmap supports a variety of scan techniques. The most common scan technique is the syn scan. A syn scan sends a SYN packet to each port on the target host. If the port is open, the target host will respond with a SYN-ACK packet. Nmap then sends an RST packet to the target host to terminate the connection. Following are the scanning techniques used in Nmap:
Once you understand the target specification and scanning techniques, Nmap has essential commands that help you in multiple scenarios such as port specification and operation system detection. The following are given commands described below:
Port Specification
Nmap can scan a single port, a range of ports, or all ports. To specify a port, use the -p option. For example, to scan port 80 which is considered an HTTP port on the target host, you would use the following command:
nmap -T 192.168.1.1 -p 80
To scan a range of ports, use the -p option followed by a comma-separated list of ports. For example, to scan ports 80 an HTTP port, 443 an HTTPS port, and 22 a default SSH Port on the target host, you would use the following command:
nmap -T 192.168.1.1 -p 80,443,22
To scan all ports, you can use the -A option.
Service and Version Detection
Nmap can detect the services that are running on open ports. To enable service detection, use the -sV option. For example, to scan port 80 on the target host and detect the service that is running, you would use the following command:
nmap -T 192.168.1.1 -p 80 -sV
Operating System Detection
Nmap can detect the operating system that is running on the target host. To enable OS detection, use the -O option. For example, to scan the target host and detect the operating system, you would use the following command:
nmap -T 192.168.1.1 -O
Timing and Performance
Nmap can be configured to scan targets quickly or slowly. To scan targets quickly, use the -T4 option. To scan targets slowly, use the -T0 option. You can also use the -T option to specify a specific timing template.
It is important to note that Nmap can be used to scan networks without permission. This can be illegal or unethical, so it is important to only scan networks that you have permission to scan.
Nmap is a powerful network discovery and security auditing tool. The essential Nmap commands and options provide you with the target specification and scanning techniques with the important commands that will give you a good starting point for using Nmap to scan networks and gather information about target hosts.
Nmap is commonly used in scanning networks, you can practice these commands on our server. Ultahost VPS hosting plan offers you an easy-to-manage, reliable, and economical hosting plan for businesses of all sizes.