How to Install RubyMine on Ubuntu
RubyMine is an IDE specifically for Ruby and Rails deve...
When it comes to securely managing sensitive data such as API keys, database credentials, and encryption keys on Ubuntu, **HashiCorp’s Vault** is the go-to solution. As a powerful tool designed to securely store and manage sensitive data, Vault provides a robust security layer to protect Ubuntu users’ most critical information. By installing Vault on Ubuntu, users can ensure that their sensitive data is safely encrypted, easily accessible, and strictly controlled.
Vault’s primary purpose is to act as a centralized secrets management system, allowing Ubuntu users to store and retrieve sensitive data with ease. With Vault, users can generate and manage encryption keys, securely store sensitive data, and even automate the rotation of credentials. To install Vault Ubuntu, users can enjoy a robust and scalable secrets management solution that will help protect their sensitive data from unauthorized access and breaches.
Installing Vault on Ubuntu can be a seamless process when using a package manager. This approach not only simplifies the installation but also ensures that dependencies are automatically configured, saving you time and effort. In this section, we’ll walk you through the step-by-step process of installing Vault using a package manager on Ubuntu.
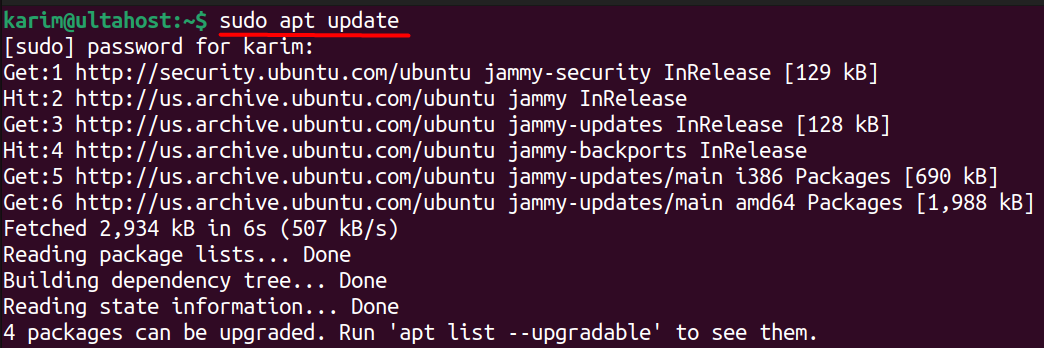
Before Vault installation on Ubuntu, it’s essential to check Ubuntu version and package manager are up-to-date. This is a critical step that prevents potential installation errors. To update your local package index, run the following command in your terminal:
sudo apt update
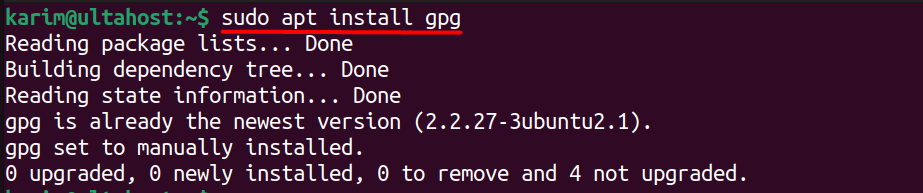
Next, you’ll need to install GPG (GNU Privacy Guard) if it’s not already installed on your system. GPG plays a vital role in verifying the authenticity of packages, ensuring that your system only installs trusted software. To install GPG, use the following command:
sudo apt install gpg
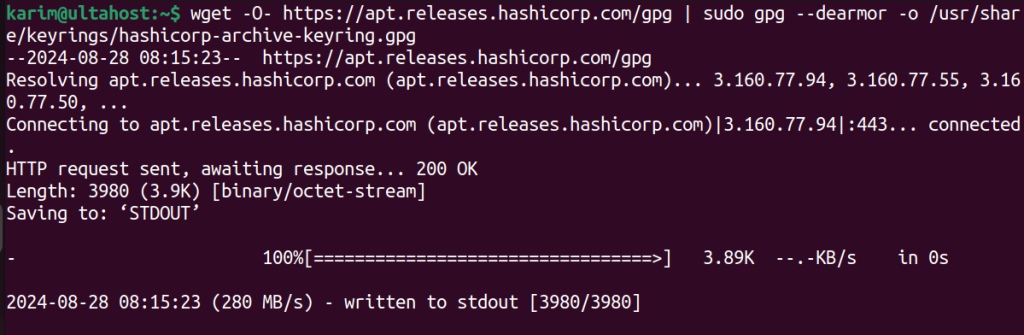
To verify the authenticity of the Vault package, you’ll need to download a keyring from HashiCorp’s website. A keyring is a file that contains cryptographic signatures for packages, which helps your system verify their authenticity. To download the keyring, use the following command:
wget -O- https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
Let’s break down what this command does:
sudo gpg --dearmor -o.hashicorp-archive-keyring.gpg in the /usr/share/keyrings/ directory.To confirm that the downloaded keyring is authentic, run the following command:
gpg --no-default-keyring --keyring /usr/share/keyrings/hashicorp-archive-keyring.gpg --fingerprint
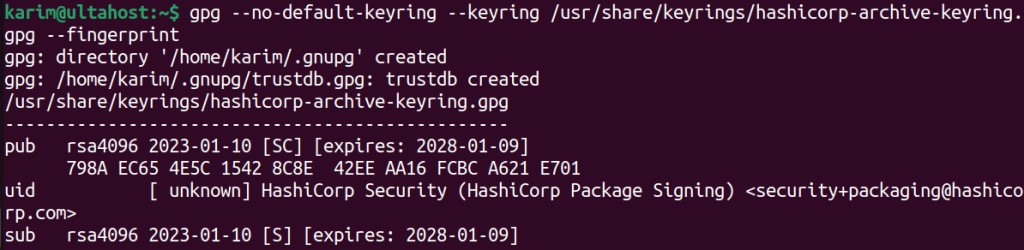
This command instructs GPG to examine the specified keyring file and display the fingerprint associated with its keys.
Next, you’ll need to add the HashiCorp repository to your system’s list of package sources. To do this, use the following command:
echo "deb [arch=$(dpkg --print-architecture) signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
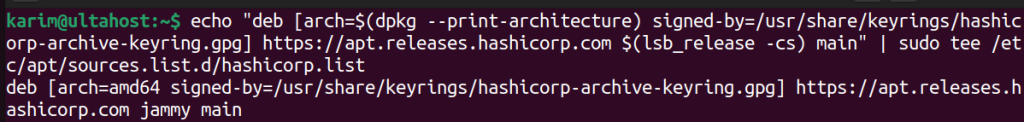
Here’s what this command does:
/etc/apt/sources.list.d/hashicorp.list using sudo tee. This ensures that the package manager recognizes the HashiCorp repository as a valid source.Once you’ve added the HashiCorp repository, update your package manager again using the following command:
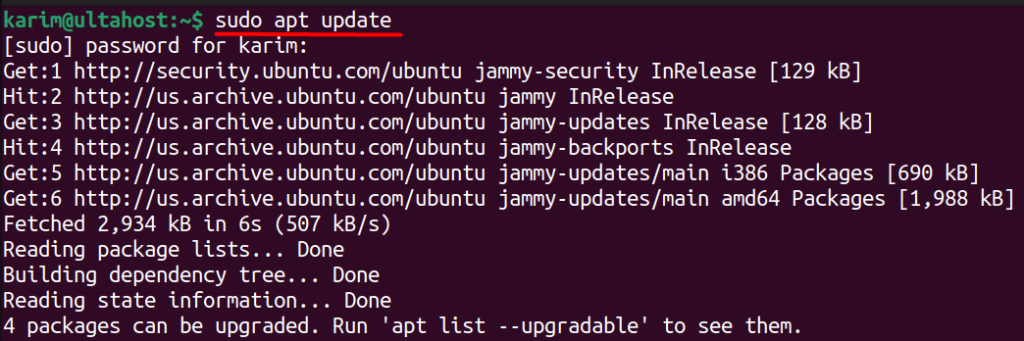
sudo apt update
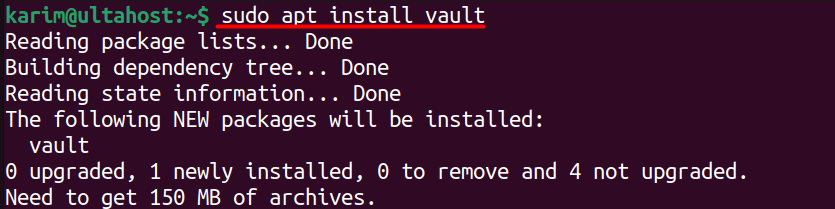
Finally, install Vault using the following command:
sudo apt install vault
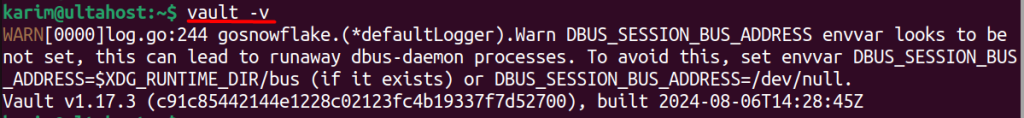
To verify that the installation was successful, run the following command:
Vault -v
That’s it! With these steps, you can successfully configure Vault Ubuntu on your system using a package manager.
Unlock the power of Ubuntu VPS
Experience the reliability of the world’s leading Linux distribution combined with the flexibility of a virtual server. Enjoy lightning-fast speeds and minimal latency.
Before diving into the installation process, it’s essential to understand the key features that make Vault a popular choice for secrets management:
Vault can generate secrets on-demand for certain systems, such as AWS or SQL databases. This means that instead of storing static, long-lived secrets, Vault can create secrets that expire automatically after a certain period.
Vault provides a mechanism to encrypt and decrypt data without having to store the sensitive data locally. This feature ensures that data at rest and in transit are protected.
Vault issues secrets with a lease, which defines a time-to-live (TTL) for the secrets. Users can renew the lease if they need the secret for a longer period, providing an additional security layer by ensuring secrets don’t remain valid indefinitely.
Vault can revoke not just individual secrets, but a set of secrets at once. This is crucial for maintaining security in the event of a breach, as it allows administrators to quickly invalidate any compromised secrets.
Vault provides detailed audit logs covering all operations. This helps in tracking access patterns and potential unauthorized access attempts.
Learn also How to Install Terraform on Ubuntu 22.04
Vault’s encryption capabilities ensure that sensitive data is protected both at rest and in transit. This makes Ubuntu systems more resilient against data breaches and unauthorized access.
With Vault, managing secrets becomes more streamlined. Users can centrally control access policies, reducing the complexity of managing secrets across multiple applications and services.
Vault is designed to scale with your needs. Whether you are managing secrets for a small application or a large infrastructure, Vault can handle the load without compromising on performance.
By automating the generation and rotation of secrets, Vault reduces the risk of human error and ensures that secrets are regularly updated, minimizing the attack surface for potential threats.
Now that Vault is installed, here are some best practices to help you use it effectively:
Before using Vault, initialize it by storing the unsealed keys and root tokens in a secure location. This is crucial for setting up your Vault server properly.
Always enable TLS to encrypt data in transit. This prevents eavesdropping and ensures that communication between clients and the Vault server is secure.
Sometimes you may encounter issues when installing Vault. Here are some common problems and their solutions:
If you encounter an error related to missing GPG keys, ensure that the keyring was downloaded and installed correctly. Re-run the keyring installation command and verify its authenticity.
If the repository is not recognized, double-check the repository configuration file /etc/apt/sources.list.d/hashicorp.list for typos or errors. Ensure the file content matches the command provided in Step 4.
If the vault command is not recognized, ensure that the installation is completed successfully. You may need to check the PATH environment variable to confirm that the Vault binary is included.
Installing HashiCorp Vault on Ubuntu using a package manager is an efficient and reliable method that simplifies the process, ensuring all dependencies are handled automatically. By following the step-by-step guide outlined in this article, you can seamlessly set up a Vault Ubuntu server, enabling secure management of sensitive data like API keys and database credentials.
This method uses trusted repositories and keyrings to verify the authenticity of packages, enhancing security from the start. Once installed, Vault provides a robust platform for centralized secrets management, contributing significantly to your system’s security posture. With Vault in place, Ubuntu users can efficiently protect their critical information from unauthorized access, ensuring data security and confidentiality.
If you are starting your journey and trying to dive into the operating system consider that you ensure your current setup can handle the demands of your specific needs. This is where you need a powerful and reliable platform like Ultahost. We provide affordable Linux VPS which helps to manage your server and dedicated resources for guaranteed speed and stability to perform your required task.
HashiCorp Vault is a tool for securely accessing secrets, managing sensitive data, and controlling access to various systems and services. It provides capabilities like secrets management, identity-based access, and encryption as a service.
Vault requires a minimum of Ubuntu 18.04 LTS or later. Ensure you have at least 512 MB of RAM and a basic network connection for downloading and installing packages.
You can download the Vault binary from the HashiCorp releases page. Use the following commands:
wget https://releases.hashicorp.com/vault/<version>/vault_<version>_linux_amd64.zip
Replace <version> with the desired Vault version.
Execute the following commands in a terminal one by one.
wget https://releases.hashicorp.com/vault/<version>/vault_<version>_linux_amd64.zip
unzip vault_<version>_linux_amd64.zip
sudo mv vault /usr/local/bin/
vault –version
Initialize vault
vault operator init
Unseal Vault:
vault operator unseal
By default, the Vault UI is accessible at http://<your-server-ip>:8200. Open a web browser and navigate to this address to access the UI. Ensure the Vault server is properly configured to listen on this port.
Use the following command to check the status of Vault:
vault status